Calculo De Antennae Para Wifi Thermostat
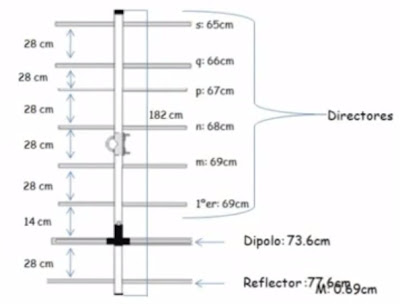
Calculo de Antenas II. Antena 2 Dipolos en X. Construccion BALUM 1.6 Para Dipolo ( EA2CMW-Richi) Articulo en Word, sobre Enfasamiento de Antenas ( EA2CMW). Erkunde Janis Asarinss Pinnwand „Electric“ auf Pinterest. Weitere Ideen zu Arduino, Diagramm und Elektrotechnik.
Terms related to cloud computing, including definitions about on-demand, distributed computing and words and phrases about software-as-a-service, infrastructure-as-a-service and storage-as-a-service. Source: • - In business, 3PL has a broad meaning that can be applied to any service. • - In business, 3PL has a. • - Amazon Cloud Drive is an online storage s. • - Amazon Dynamo Databas. • - The Amazon Elastic Co.
• • • - The Amazon Simple S. • • - XaaS is a collective term that stan. • - Apache Cassandra is an open source distribute. • - Apache ZooKeeper is an open source file appli. • - Appliance computing is an Internet-base. • - Application migration is the proces. • - AT&T Syna.
• - Automated data tiering is a type. • - Automated provisioning is the abi. • - Auto-scaling, also spelled autoscaling, is a cloud comp. Fgtech V54 Keygen Software. • - Big data as a servi. • • - Apache Cassandra is an open source distributed database sys. • - Apache Cassandra is a. • - CenturyLink is a worldwide telephone service provider a.
• - Google Chromebook is a thin client laptop that is configu. • - Cisco Borderless Networks i. • - Cisco Cloud Builder is one of three tra. • - The Cisco Cloud Partner. • - The Citrix Cloud Pr. • - A cloud adaptor is a software utility that controls. • - A cloud broker is a third-party individual or business.
• - A cloud aggregator is a type of cloud broker. • - Cloud analytics is a service model in which one. • - A cloud application (or cloud app) is an ap. • • - Cloud archive is a storage procurement model in whi.
• - Cloud backup, also known as online backup, is a strat. • - Cloud backup, also kn.
• - A cloud broker is a third-party individual or busines. • - A cloud broker is a third. • - Cloud bursting is an application deployment model.
• - Cloud cartography is a scheme for pinpointi. • - The Cloud Controls Matrix is a base.
• - Cloud Data Mana. • - A cloud database is a database that has been opti. • - A cloud database is a database that has been opti. • - Cloud disaster recovery (cloud. • - Cloud dis. • - Cloud disaster recovery (cloud DR) is a component of a disast.
• - A cloud drive is an umbrella term used to describe any. • - Cloud drive storage is a term that refe. • - Cloud ecosystem is a term used to describe the. • - Cloud ERP is an approach to enterprise resource planning (E. • - Cloud federation is the practice of interconn. • - A federated cloud (also called cloud federati.
• - Cloud file storage is a storage service t. • - A cloud-in-a-can, also called a cloud in a box, i. • - A cloud-in-a-can, also called a cloud in a box, i. • - The Cloud Industry Forum (CIF) is a c. • - Cloud insurance is an approach to risk manageme. • - Cloud integration is the process of configu. • - A cloud integration platf.
• - A cloud integrator is a product or service th. • - Cloud migration is the process of moving data.
• - Cloud NAS (network attached storage) is remote storage that. • • - Cloud NAS (networ.
• - A cloud orchestrator is software that man. • - Cloud portability is the ability to move ap. • - A cloud provider is a company that offers some co.
• - A cloud provider API is an application pr. • - Cloud provisioning is user account provis. • - The Cloud Security Alliance (CS. • - The Cloud Security. • - Cloud seeding (also known as seeding the cloud) is. • - Cloud services governance is. • - Cloud service migration is the.
• - A cloud service is any resource that is provided. • - A cloud services reseller is a. • - Cloud storage is a service model in which data is m. • - A cloud storage API is an application progr. • - A cloud storage appliance is a.
• - Cloud storage backup involves moving. • - Cloud storage encryption is t. • - A cloud storage gateway is a hardwa.
• - A cloud storage infra. • - Cloud storage providers are third. • - A cloud storage service is a busine. • - A cloud storage SLA is a service-level agre. • - Cloud washing is the purposeful and sometimes decep. • - A cloud-in-a-can, also called a cloud in a box, i. • - A cloud-in-a-ca.
• - A cloud-ori. • - Cloud-to-cloud migration (C2C.
• - CloudAudit is a specification for the presentation of inf. • - CloudAV is a program that combines multiple antivirus applicati. • - A cloudbook is a thin client notebook computer with a brows. • - Cloudburst VM (virtual machine) escap. • - Cloudsourcing is an arrangement in which a company.
• - CloudSwitch is a company that makes cloud migration sof. • - Cloudware is software that runs on a remote Web server rath. • - In general, collocation is moving or placing things tog. • - In general, collocation is moving or placing things tog. • • - A Common Service Center (CSC) is an.
• - A Common Service Center. • - A community cloud is a multi-tenant infrastruct. • - Computing arbitrage is a cloud services. • - A consumption-b. • - Converged infrastructure is a.
• - The Cloud Security Alliance (CSA) is a nonprofit organization that prom. • - A Common Service Center (CSC) is an information and communication techn. • - D2D2C (disk-to-disk-to-cloud) is an approach to hybrid cloud backup. • - D2D2C (disk-to-disk. • - Desktop as a service (DaaS), also called virtual desktop or hosted de. • - Data as a Service (DaaS) is an information. • - A data center as a service (D.
• - A data center. • - Data federation technology, a. • - Data federation technolog. • • - Data portability is the ability to move data. • - A data silo is a repository of fixed data that an organizat.
• - Data federation t. • - A cloud database is a database that. • - A data center as a service (DCaaS) provider will supply turnkey phy. • - In general, a decoupled architect. • - Deep analytics is the application of sophisticate. • - Dell Boomi is a Software as a Service (SaaS) integration.
• - Desktop as a service (DaaS), also cal. • - Desktop as a service (D. • - D2D2C (disk-to-disk-to-cloud) is an.
• - D2D2C (disk-to-disk-to-cloud) is an. • - Dolphin ArchiveLink Enabler (ALE) is an SAP ABAP add-on. • - Dropbox is a cloud storage provider (sometimes referred to as a. • - Elastic load balancing (ELB) is a. • - EMC Cloud A. • • - EMC Cloud Architect Certification (EMCCA) is a certification and tr. • - End user computing platfo.
• • - End user computing platform (EUC platform) is a marketing buzzword that. • - End user computing platform (EUC platform) is a marke. • - Eucalyptus is a software platform for implementing Infras.
• • - An event-driven application i. • - Exchange Online is the hosted version of Micros.
• - The Azure Fabric Controller (FC) is the part of the Windows Azure platfor. • - A federated cloud (also called cloud federation. • - A federat. • - Force.com is a Platform as a Service (PaaS) product designe.
• - G-Cloud, or Government Cl. • - In the telecommunications industry, gigabyte (GB) billing.
• - Geo-replication is a type of data storage repli. • - Amazon Glacier is a low-cost. • - Google Apps for Business is a. • - Google Chrome OS is an open source lightweigh. • - Google Drive is a cloud storage service that offers 5.
• - The United Stat. • - Green cloud is a label that describes the potential env. • - Grid computing (or the use of a computational gri.
• - A guest virtual machine (guest VM). • - A guest virtu. • - A guest virtual machine (guest VM) is the software component. • - Hadoop is a free, Java-based programming framework that supports.
• - Heroku is a cloud-based development platform as a service (PaaS). • - Hosted CRM is an arrangement in which a company outsource. • - A hosted virtual desk.
• - Hot desking is a work space sharing model in which empl. • • - An HTML5 desktop client is a type o. • - Hybrid cloud hosting allows organizat. • - Hybrid cloud storage is an approach t. • - Hybrid IT is an approach to enterprise computing in which a. • - Hyper-V Cloud is a combination of Microsoft virtual.
• - Infrastructure as a Service is a provision model in which an organiza. • - IBM SmartCloud is a line of enterprise-class clou. • - iCloud is an Apple email, storage and data synchronization subscr. • - Infrastructure as a Ser.
• - Infrastru. • - Integration as a Service (Iaa. • - Private cloud storage, also calle. • - The Internet of Things is a scenario in w.
• - Jamcracker Services Delivery Network (JSDN) is a platform. • - Jitterbit is a commercial software integration product that. • - Kapow is a company that provides an API (application program interf. • - MapReduce is a software framework that allows developers to. • - The Microsoft Office 365. • - The mobile cloud is Internet-based data, applications.
• - Multi-cloud strategy is the concomita. • - A native cloud application (N. • - A native cloud ap. • - A native cloud application (NCA) is a program that is specifically desi. • - Nebula is an open source cloud computing program that provides on. • - NetMagic Solutions is an India-based IT h. • - Citrix NetScaler SDX is a service delivery netw.
• - NoOps (no operations) is the concept that an IT environment can bec. • - NoSQL database, also called Not Only SQL, is an approach to data ma.
• - NoSQL database, also called Not Only. • - NoSQL database, also called Not Only SQL, is an appro. • - A handy g. • - On-demand (OD) computing is an increasi.
• - Cloud backup, also known as online backup, is a str. • - An open API, sometimes referred to as a public API, is an app. • - The Open Grid S. • • - Open Virtualization Forma. • - OpenStack is an open source infrastructure as a service (Ia. • - Chef is an open-source systems management and cloud i.
• - Platform as a Service (PaaS) is a way to rent hardware, operating sys. • - Amazon's PayPhrase is an Internet point-of-sale (POS) short.
• - Personal cloud storage (PCS) is an online web service that provides ser. • - Personal cloud storage (PCS) is a.
• - Personal cloud storag. • - Platform as a Service (PaaS) is a w. • - Platform as a Service. • - A portable application (portable app) is a software p.
• - Private cloud storage, also called. • • - In general, provisioning means 'providing' or making. • - A public cloud is one based on the standard cloud com. • - Public cloud storage, also called sto. • - Rapid Access Computing Environment (RACE) is a United States federal. • - Racemi is a data center software vendor that specializes in cloud.
• - Rapid Acc. • • - A Red Hat Cer. • - The Red Hat Cloud P. • - Red Hat Storage is a new distribute. • - Software as a Service (SaaS) is a software distribution model in whic. • - Security-as-a-service (SaaS) is an outsourcing model for security man.
• - Software as a Service business intelligence (SaaS BI) is a deli. • - SaaS ERP is a hosting model for enterprise resource planning.
• • - SPI is an acronym for the most common cloud compu. • - SaaSGrid is an application server and integrated framework fo. • - The Same Origin Policy (SOP), also called. • - The Same Origin Policy (SOP). • - Security-as-a-service (SaaS) is an. • - Security-as-a-service.
• • - Sharding is a type of database partitioning that is used to s. • - Single-tenancy is an architecture in which a sing. • - SlapOS (Simple Language for Accounting and Provisioning Operating.
• - SnapLogic is a software company that offers cloud integrati. • - Vertical SaaS describes a type of S. • - Software as a Service (SaaS) is a s. • - Software as a Service.
• - Software as a Service busines. • - Software. • - SaaS ERP is. • - SaaS ERP is. • - The Same Origin Policy (SOP), also called Single Origin Policy, is a se. • - SPI is an acronym for the most common cloud computing servi. • - SPI is an acronym for.
• - The Security, Trust and Assurance Registry (STAR) is an online regist. • - A stateless app is an application program that does.
• - A streaming application is a progra. • • - A telecom cloud provider is a tel. • - In business, 3PL has a broad meanin. • - In business, 3PL has a broad meanin.
• - The Trusted Cloud Initiative. • - Tsunami UDP is an open source file transfer protocol th.
• - A turnkey cloud is a product that includes pre-test. • - A unified computing system (UCS) is a data center architecture that int. • - A unified computing system (U.
• - A unified computi. • - User self-provisioning, also know.
• - Utility storage is a service model in which a p. • - Vendor lock-in is a situation in which a customer. • - Vertical SaaS describes a type of Software as a Ser.
• - A virtual firewall is a software appliance th. • - A virtual private cloud (VPC) is a. • - WAN optimization, also known as WAN accelerat. • - A WAN accelerator is an appliance that improves. • - WAN optimization, also known as WAN accelerat. • - A white label cloud service.
• - The Azure Fabri. • - Windows Intune is a cloud-based desktop managemen. • - Windows Live SkyDrive is a free onl. • - XaaS is a collective term that stands for a number of things includin. • - XaaS is a collective. • - Zero client, also known as ultrathin client, is a serve.
Cloud IoT and IT Security More organizations are deploying Internet of Things devices and platforms to improve efficiency, enhance customer service, open up new business opportunities and reap other benefits. But the IoT can expose enterprises to new security threats, with every connected object becoming a potential entry point for attackers. This eBook will discuss: • What to expect from IoT security standardization efforts; • Whether current generation systems, like mobile device management software, will help; • How to approach networking to keep corporate systems secure; and • Ho w to make sure the cloud components of your IoT implementations are secure. Please read the attached ebook.
Cloud Mechanics: Delivering Performance in Shared Environments By: Expedient Data Centers, a leader in Managed and Data Center Services with locations from Cleveland to Memphis to Boston, unpacks the mechanics of how it consistently meets Service Level Agreements for its customers. This whitepaper explores how service providers use VMTurbo to provide consistent performance across all workloads, as well as the three roles a responsible managed service provider (MSP) takes in order to accomplish that directive. Please read the attached whitepaper. Cloud Orchestrator Posted by A cloud orchestrator is software that manages the interconnections and interactions among -based and on-premises business units. Cloud orchestrator products use to connect various automated processes and associated resources. The products usually include a management.
To orchestrate something is to arrange various components so they achieve a desired result. In an IT context, this involves combining tasks into workflows so the provisioning and management of various IT components and their associated resources can be automated. This endeavor is more complex in a cloud environment because it involves interconnecting processes running across heterogeneous systems in multiple locations. Cloud orchestration products can simplify the intercomponent communication and connections to users and other apps and ensure that links are correctly configured and maintained. Such products usually include a Web-based portal so that orchestration can be managed through a single pane of glass.
When evaluating cloud orchestration products, it is recommended that administrators first map the workflows of the applications involved. This step will help the administrator visualize how complicated the internal workflow for the application is and how often information flows outside the set of app components. This, in turn, can help the administrator decide which type of orchestration product will help automate workflow best and meet business requirements in the most cost-effective manner. Orchestration, in an IT context, is the automation of tasks involved with managing and coordinating complex software and services.
The endeavor is more complex in a cloud environment because it involves interconnecting processes running across heterogeneous systems in multiple locations. Processes and transactions have to cross multiple organizations, systems and. The goal of cloud orchestration is to, insofar as is possible, automate the configuration, coordination and management of software and software interactions in such an environment. The process involves automating workflows required for service delivery. Tasks involved include managing server, directing the flow of processes among applications and dealing with exceptions to typical workflows. Vendors of cloud orchestration products include Eucalyptus, Flexiant, IBM, Microsoft, VMware and V3 Systems. The term “orchestration” originally comes from the study of music, where it refers to the arrangement and coordination of instruments for a given piece.
Continue Reading About cloud orchestrator • • • • Related Terms API management is the process of publishing, promoting and overseeing application programming interfaces (APIs) in a secure. A data silo exists when an organization's departments and systems cannot, or do not, communicate freely with one another and. An open API, sometimes referred to as a public API, is an application program interface that provides a developer with. Dig Deeper on Cloud data integration and application integration.
On-premises: Finding the right balance By The process of figuring out which apps work in the cloud vs. On-premises doesn't yield the same results for everyone. Greg Downer, senior IT director at Oshkosh Corp., a manufacturer of specialty heavy vehicles in Oshkosh, Wisc., wishes he could tip the balance of on-premises vs. Cloud more in the direction of the cloud, which currently accounts for only about 20% of his application footprint. However, as a contractor for the Department of Defense, his company is beholden to strict data requirements, including where data is stored. 'Cloud offerings have helped us deploy faster and reduce our data center infrastructure, but the main reason we don't do more in the cloud is because of strict DoD contract requirements for specific types of data,' he says.
In Computerworld's of 196 IT managers and leaders, 79% of respondents said they have a cloud project underway or planned, and 58% of those using some type of cloud-based system gave their efforts an A or B in terms of delivering business value. Downer counts himself among IT leaders bullish on the cloud and its potential for positive results. 'While we don't have a written cloud-first statement, when we do make new investments we look at what the cloud can offer,' he says. Oshkosh has moved some of its back-office systems, including those supporting human resources, legal and IT, to the cloud. He says most of the cloud migration has been from legacy systems to software as a service (SaaS). For instance, the organization uses ServiceNow's SaaS for IT and will soon use it for facilities management.
According to the Forecast report, a third of respondents in the next 12 months. Cordell Schachter, CTO of New York City's Department of Transportation, says he allies with the 22% of survey respondents who plan to increase investments in a hybrid cloud computing environment. The more non-critical applications he moves out of the city's six-year-old data center, the more room he'll have to support innovative new projects such as the, a joint effort with the U.S. Department of Transportation's Intelligent Transportation Systems Joint Program Office. The Connected Vehicle project, in the second year of a five-year pilot, aims to use dedicated short-range communication coupled with a network of in-vehicle and roadway sensors to automatically notify drivers of connected vehicles of traffic issues.
'If there is an incident ahead of you, your car will either start braking on its own or you'll get a warning light saying there's a problem up ahead so you can avoid a crash,' Schachter says. The program's intent is to reduce the more than that occur in the U.S. Supporting that communication network and the data it generates will require more than the internal data center, though. Schachter says the effort will draw on a hybrid of on-premises and cloud-based applications and infrastructure. He expects to tap a combination of platform as a service, infrastructure as a service, and SaaS to get to the best of breed for each element of the program. 'We can use the scale of cloud providers and their expertise to do things we wouldn't be able to do internally,' he says, adding that all providers must meet NYC DOT's expectations of 'safer, faster, smarter and cheaper.' Apps saved for on-premises In fact, Schachter has walled off only a few areas that aren't candidates for the cloud -- such as emergency services and email.
'NYC DOT is one of the most sued entities in New York City, and we constantly need to search our corpus of emails. We have a shown a net positive by keeping that application on-premises to satisfy Freedom of Information Law requests as well as litigation,' he says. The City of Los Angeles also has its share of applications that are too critical to go into the cloud, according to Ted Ross, CIO and general manager of the city's Information Technology Agency. For instance, supervisory control and data acquisition (SCADA), 911 Dispatch, undercover police operations, traffic control and wastewater management are the types of data sets that will remain on-premises for the foreseeable future. 'The impact of an abuse is so high that we wouldn't consider these applications in our first round of cloud migrations. As you can imagine, it's critical that a hacker not gain access to release sewage into the ocean water or try to turn all streetlights green at the same time,' he says. The cloud does serve as an emergency backup to the $108 million state-of-the-art emergency operations center.
'If anything happens to the physical facility, our software, mapping and other capabilities can quickly spin up in the cloud,' he says, adding that Amazon Web Services and Microsoft Azure provide many compelling use cases. The city, with more than 1,000 virtual servers on-premises, considers the cloud a cost-effective godsend. 'We very much embrace the cloud because it provides an opportunity to lower costs, makes us more flexible and agile, offers off-site disaster recovery, empowers IT personnel, and provides a better user experience,' he says. SaaS is a gateway drug to other cloud services.
Ted Ross, CIO, city of Los Angeles As an early adopter of Google's Gmail in 2010, Ross appreciates the value of the cloud, so much so that in 2014, the city made cloud a primary business model, starting with SaaS, which he calls 'a gateway drug to other cloud services.' Eventually, the city ventured into infrastructure as a service, including using 'a lot of Amazon Web Services,' which Ross describes as more invasive than SaaS and more in need of collaboration between the service provider and the network team. 'You have to be prepared to have a shared security model and to take the necessary steps to enact it,' he says. Cloud computing also requires additional network bandwidth to reduce latency and maximize performance, he adds.
Other reasons for saying no to the cloud As much as Ross is a cloud promoter, he says he fully understands the 21% of respondents to Computerworld's Forecast survey who say they have no plans to move to the cloud. 'I get worried when users simply want to spin up anything anywhere and are only concerned about functionality, not connectivity and security.' Ron Heinz, founder and managing director of venture capital firm Signal Peak Ventures, says there will always be a market for on-premises applications and infrastructure. For instance, one portfolio client that develops software for accountants found that 40% of its market don't want to move their workflow to the cloud. Heinz attributes the hesitation to more mature accounting professionals and those with security concerns. 'Everybody automatically assumes there is a huge migration to the cloud.
But there will always be a segment that will never go the cloud as long as you have strong virtual private networks and strong remote access with encrypted channels,' he says. Greg Collins, founder and principal analyst at analyst firm Exact Ventures, has found clients usually stick with on-premises when they are still depreciating their servers and other gear. 'They have the attitude 'if it ain't broke, don't fix it,' he says. Still, he also believes the cloud is still in the early days and will only grow as the installed base of on-premises equipment hits end of life. Performance gains 'We have seen a significant shift in the last couple of years in the interest for public cloud,' says Matthew L.
Taylor, managing director of consulting firm Accenture Strategy. Accenture, a company of more than 394,000 employees, has most of its own applications hosted in the public cloud.
Many of his clients are not moving as fast. 'I wouldn't say the majority of our clients' application loads are in the public cloud today; that's still the opportunity,' he says.
Of the clients that have moved to the cloud, very few have gone back to on-premises. 'If they did, it wasn't because the cloud-based capabilities were not ready; it was because the company wasn't ready and hadn't thought the migration, application or value case through,' Taylor says, adding that others who floundered did so because they couldn't figure out how to wean off their legacy infrastructure and run it in tandem with the cloud. Most of his clients have been surprised to find that lower service costs have not been the biggest benefit of the cloud. 'In the end, savings don't come from technology tools, they come from operational shifts and performance gains,' he says. For instance, a bank in Australia that he wouldn't name moved a critical application to the cloud but had two other applications on-premises, causing performance problems.
The performance problems arose because the cloud app relied heavily on the on-premises applications, so performance was slowed as they tried to communicate with one another. Once the bank moved all three applications to the cloud, it found the applications had never performed better, and downtime and maintenance improved. Kas Naderi, senior vice president of Atlanticus Holdings Corp., a specialty finance company focused on underserved consumers in the U.S., U.K., Guam and Saipan, had a similar experience when the company 'lifted and shifted' its entire application portfolio to the cloud. 'Every one of our applications performed as good or better than in our data center, which had hardware that was ten years old,' he says. In 2014, the company took all existing applications and ran them 'as is' in the cloud environment.
Atlanticus relied on consulting firm DISYS to not only validate Atlanticus' migration approach, but also to help staff a 24-hour, 'follow the sun' implementation. 'They enabled us to accelerate our timeline,' he says. In addition, DISYS, an Amazon Web Services partner, lent its expertise to explain what would and wouldn't work in Amazon's cloud. Atlanticus deployed a federated cloud topology distributed among Amazon Web Services, Microsoft Azure, Zadara cloud storage, InContact Automatic Call Distribution, and Vonage phone system, with applications sitting where they operate best -- such as Microsoft Active Directory on Azure. The company front-ends Amazon Web Services with a private cloud that handles security tasks including intrusion detection/prevention and packet inspection. 'There is an absolute need for private cloud services to encapsulate a level of security and control that might not be available in the public cloud,' Naderi says.
In its next phase of cloud migration, Atlanticus will assess whether legacy applications have SaaS or other cloud-based alternatives that perform even better. In other words, the company took all its applications 'as is,' including legacy, and put them in the cloud.
Now they are going to see if there are better alternatives to those legacy apps available to adopt. Oshkosh ran a similar exercise and found that cloud-based SharePoint outperformed on-premises SharePoint and improved functionality. For instance, the company has been able to create a space where external suppliers can interact with internal employees, safely exchanging critical information. 'That was challenging for on-premises,' Downer says. He adds: 'We also are using various CRM cloud applications within some segments, and have started to meet niche business requirements on the shop floor with cloud solutions.'
Staffing the cloud As organizations move to the cloud, they sometimes harbor the misconception that migration means they need fewer IT staff. These IT leaders say that's not the case.
Instead, they've gotten more value out of their skilled workforce by retraining them to handle the demands of cloud services. Greg Downer, senior IT director at specialty vehicle manufacturer Oshkosh Corp.: 'We retrained our legacy people, which went well. For instance, we trained our BMC Remedy administrators on the ServiceNow SaaS. We're not just using 10% to 20% of a large on-premises investment, but getting the full value of the platform subscription we are paying for.' Kas Naderi, senior vice president of technology, specialty finance company Atlanticus Holdings Corp.: 'Our staff used to be extended beyond the normal 40-hour week, handling ad-hoc requests, emergencies, upgrades, security, etc.
We were blessed to have a very flexible and high-IQ staff and were happy to shift their day-to-day responsibilities away from upkeep and maintenance to leadership of how to best leverage these cloud-based platforms for better quality of service. We have become a lot more religious on operating system upgrades and security postures and a lot more strategic on documentation and predictability of services. We went from racking and stacking and maintaining the data center to a business purpose.' Ted Ross, general manager of information technology and CIO, city of Los Angeles: 'Moving to the cloud requires a sizeable skills change, but it's also a force multiplier that lets fewer hands do a lot more. We're not a start-up; we're a legacy enterprise. Our data center had a particular set of processes and its own ecosystem and business model.
We want to continue that professionalism, but make the pivot to innovative infrastructure. We still have to be smart about data, making sure it's encrypted at rest, and working through controls.
The cloud expands our ecosystem considerably, but of course we still don't want to allow critical information into the hands of the wrong people.' -- Sandra Gittlen Related: • • • •. Cmdlet A cmdlet (pronounced 'command-let') is a Windows that performs a single.
A, in this context, is a specific order from a user to the computer's or to an to perform a service, such as 'Show me all my files' or 'Run this program for me.' Although Windows PowerShell includes more than two hundred basic core cmdlets, administrators can also write their own cmdlets and share them. A cmdlet, which is expressed as a verb-noun pair, has a.ps1 extension.
Each cmdlet has a that can be accessed by typing Get-Help -Detailed. The detailed view of the cmdlet help file includes a description of the cmdlet, the command, descriptions of the and an example that demonstrate the use of the cmdlet. Popular basic cmdlets include: Cmdlet Function Get-Location get the current directory Set-Location change the current directory Copy-Item copy files Remove-Item remove a file or directory Move-Item move a file Rename-Item rename a file New-Item create a new empty file or directory Link. Posted by Common Vulnerabilities and Exposures (CVE) provides unique identifiers for publicly known security threats.Common Vulnerabilities and Exposures (CVE) is a catalog of known security threats. The catalog is sponsored by the United States Department of Homeland Security (), and threats are divided into two categories: vulnerabilities and exposures. According to the CVE website, a vulnerability is a mistake in software code that provides an attacker with direct access to a system or network. For example, the vulnerability may allow an attacker to pose as a or who has full access.
An exposure, on the other hand, is defined as a mistake in software code or that provides an attacker with indirect access to a system or network. For example, an exposure may allow an attacker to secretly gather customer information that could be sold. The catalog's main purpose is to standarize the way each known vulnerability or exposure is identified. This is important because standard IDs allow security administrators to quickly access technical information about a specific threat across multiple CVE-compatible information sources. CVE is sponsored by US-, the DHS Office of Cybersecurity and Information Assurance ().
MITRE, a not-for-profit organization that operates research and development centers sponsored by the U.S. Federal government, maintains the CVE catalog and public Web site.
It also manages the CVE Compatibility Program, which promotes the use of standard CVE identifiers by authorized CVE Numbering Authorities (CNAs). Compliance Audit Posted by A compliance audit is a comprehensive review of an organization's adherence to regulatory guidelines. Independent accounting, security or IT consultants evaluate the strength and thoroughness of preparations. Auditors review security polices, user access controls and procedures over the course of a compliance audit.
What, precisely, is examined in a compliance audit will vary depending upon whether an organization is a public or private company, what kind of data it handles and if it transmits or stores sensitive financial data. For instance, requirements mean that any electronic communication must be backed up and secured with reasonable infrastructure. Healthcare providers that store or transmit e-health records, like personal health information, are subject to requirements. Financial services companies that transmit credit card data are subject to requirements. In each case, the organization must be able to demonstrate compliance by producing an, often generated by data from event log management software.
Compliance auditors will generally ask s, CTOs and IT administrators a series of pointed questions over the course of an audit. These may include what users were added and when, who has left the company, whether user IDs were revoked and which IT administrators have access to critical systems. IT administrators prepare for compliance audits using and robust software to allow tracking and documentation authentication and controls in IT systems.
The growing category of (governance, risk management and compliance) software enables CIOs to quickly show auditors (and s) that the organization is in compliance and will not be not subject to costly fines or sanctions. Continue Reading About compliance audit • • • • • • • • • Related Terms • - Agreed-upon procedures are the standards a company or client outlines when it hires an external party to perform an audit on. • - The Federal Accounting Standards Advisory Board (FASAB) is an advisory committee that develops accounting standards for U.S.
• - The International Accounting Standards Board is the independent standard-setting body of the IFRS Foundation. 5 ways a Connection Broker Simplifies Hosted Environments With all the moving parts to think about when moving resources into the data center, a connection broker might be the last thing on your mind.
Waiting until you've designed the rest of your data center to consider the connection broker can be detrimental to the overall usability of your system. This is why we've created our, which outlines five scenarios where including a connection broker into your design from the get-go can future-proof and improve your hosted desktop solution. Download our new eBook and learn about: • Supporting mixed virtual and physical environments • Migrating between virtualization and hosted desktop solutions • Supporting a wide range of users and use cases • And more! Please read the attached whitepaper. Converged Infrastructures Deliver the Full Value of Virtualization By Ravi Chalaka Hitachi Data Systems Satisfied with your virtualization efforts? You could be. How does an organization modernize IT and get more out of infrastructure resources?
That’s a question many CIOs ask themselves. With hundreds or even thousands of physical hardware resources, increasing complexity and massive data growth, you need new, reliable ways to deliver IT services in an on-demand, flexible and scalable fashion. You also must address requests for faster delivery of business services, competition for resources and trade-offs between IT agility and vendor lock-in. Please read the attached whitepaper.
Copyleft Copyleft is the idea and the specific stipulation when distributing software that the user will be able to copy it freely, examine and modify the source code, and redistribute the software to others (free or priced) as long as the redistributed software is also passed along with the copyleft stipulation. The term was originated by Richard Stallman and the. Copyleft favors the software user's rights and convenience over the commercial interests of the software makers. It also reflects the belief that freer redistribution and modification of software would encourage users to make improvements to it. ('Free software' is not the same as, which is usually distributed with copyright restrictions.) Stallman and his adherents do not object to the price or profit aspects of creation and redistribution of software - only to the current restrictions placed on who can use how many copies of the software and how and whether the software can be modified and redistributed.
The de facto collaboration that developed and refined and other collegially-developed programs led the FSF to the idea of 'free' software and copyleft. In 1983, the FSF began developing a 'free software' project that would both demonstrate the concept while providing value to users. The project was called GNU, an operating system similar to a Unix system. GNU and its various components are currently available and are distributed with copyleft stipulations. Using GNU components, the popular system is also issued with a copyleft.
Copyright Copyright is the ownership of an intellectual property within the limits prescribed by a particular nation's or international law. In the United States, for example, the copyright law provides that the owner of a property has the exclusive right to print, distribute, and copy the work, and permission must be obtained by anyone else to reuse the work in these ways. Copyright is provided automatically to the author of any original work covered by the law as soon as the work is created. The author does not have to formally register the work, although registration makes the copyright more visible.
(See Circular 66, 'Copyright Registration for Online Works,' from the U.S Copyright Office.) Copyright extends to unpublished as well as published works. Law extends copyright for 50 years beyond the life of the author. For reviews and certain other purposes, the 'fair use' of a work, typically a quotation or paragraph, is allowed without permission of the author. The Free Software Foundation fosters a new concept called in which anyone can freely reuse a work as long as they in turn do not try to restrict others from using their reuse. EditPros, an editing and marketing communications firm, has allowed us to reprint below an article about copyright as it applies to the Internet. Are You Violating Copyright on the Internet? The Internet, inarguably one of the most remarkable developments in international communication and information access, is fast becoming a lair of copyright abuse.
The notion of freedom of information and the ease of posting, copying and distributing messages on the Internet may have created a false impression that text and graphic materials on World Wide Web sites, postings in 'usenet' news groups, and messages distributed through e-mail lists and other electronic channels are exempt from copyright statutes. In the United States, copyright is a protection provided under title 17 of the U.S. Code, articulated in the 1976 Copyright Act.
Copyright of a creative work extends 50 years beyond the lifespan of its author or designer. Works afforded copyright protection include literature, journalistic reports, musical compositions, theatrical scripts, choreography, artistic matter, architectural designs, motion pictures, computer software, multimedia digital creations, and audio and video recordings.
Copyright protection encompasses Web page textual content, graphics, design elements, as well as postings on discussion groups. Canada's Intellectual and Industrial Property Law, Great Britain's Copyright, Designs and Patents Act of 1988, and legislation in other countries signatory to the international Berne Convention copyright principles provide similar protections. Generally speaking, facts may not be copyrighted; but content related to presentation, organization and conclusions derived from facts certainly can be. Never assume that anything is in the 'public domain' without a statement to that effect.
Here are some copyright issues important to companies, organizations and individuals. Handling of External Links Even though links are addresses and are not subject to copyright regulations, problems can arise in their presentation. If your Web site is composed using frames, and linked sites appear as a window within your frame set, you may be creating the deceptive impression that the content of the linked site is yours. Use HTML coding to ensure that linked external sites appear in their own window, clearly distinct from your site.
Incidentally, you may wish to disavow responsibility for the content of sites to which you provide links. Work for Hire While copyright ordinarily belongs to the author, copyright ownership of works for hire belong to the employer. Copyright Act of 1976 provides two definitions of a work for hire: 1. A work prepared by an employee within the scope of his or her employment; or 2. A work specially ordered or commissioned for use as a contribution to a collective work, as a part of a motion picture or other audiovisual work, as a translation, as a supplementary work, as a compilation, as an instructional text, as a test, as answer material for a test, or as an atlas, if the parties expressly agree in a written instrument signed by them that the work shall be considered a work made for hire.
Copyright Office documentation further states, 'Copyright in each separate contribution to a periodical or other collective work is distinct from copyright in the collective work as a whole and vests initially with the author of the contribution.' Employee Activities Just as making bootleg tapes of recorded music and photocopying books are illegal activities, printing and distributing contents of Web pages or discussion group postings may constitute copyright infringement. And companies may be liable for such activities conducted by their employees using company computing or photocopying equipment. However, the law does not necessarily prohibit downloading files or excerpting and quoting materials. The doctrine of fair use preserves your right to reproduce works or portions of works for certain purposes, notably education, analysis and criticism, parody, research and journalistic reporting. The amount of the work excerpted and the implications of your use on the marketability or value of the works are considerations in determining fair use.
Works that are not fixed in a tangible form, such as extemporaneous speeches, do not qualify for copyright protection. Titles of works, and improvisational musical or choreographic compositions that have not been annotated, likewise cannot be copyrighted. Names of musical groups, slogans and short phrases may gain protection as trademarks when registered through the U.S. Patent & Trademark Office. Protecting Your Own Works Although copyright automatically applies to any creative work you produce, you can strengthen your legal copyright protection by registering works with the U.S.
Copyright Office. Doing so establishes an official record of your copyright, and must be done before filing an infringement civil lawsuit in Federal district court. Registration costs $20. For information, visit the Copyright Office Web site or call (202) 707-3000; TTY is (202) 707-6737. If you appoint an independent Web developer to create and maintain your Web site, make sure through written agreement that you retain the copyright to your Web content.
Place a copyright notice on each of your Web pages and other published materials. Spell out the word 'Copyright' or use the encircled 'c' symbol, along with the year of publication and your name, as shown in this example: Copyright 1998 EditPros marketing communications If you're concerned about copyright protection in other nations, add: 'All rights reserved.' Along with your copyright notice, include an acceptable use policy, announcing to your readers how they may use the material.
You may allow Web visitors, for example, to download and print pages for their own use, but may prohibit them from distributing those materials to others without your permission. You may wish to decline permission to download graphics or sound files that you created. How to Stay Legal If you'd like to share the contents of an interesting Web page with your company employees, describe the page and tell them the URL address of the Web site so they can look for themselves. And if the latest edition of a business newspaper contains an article you'd like to distribute to your 12 board members, either ask the publication for permission to make copies, or buy a dozen copies of the newspaper. Retention of value through sales of that newspaper, after all, is what copyright law is intended to protect. Selected Links contains an explanation of American copyright basics and a list of frequently asked questions, as well as the complete text of the United States Copyright Act of 1976. Topics include copyright ownership and transfer, copyright notice, and copyright infringement and remedies.
The site is maintained by the U.S. Library of Congress. Is an online resource operated by the Copyright Clearance Center Inc. (CCC), which was formed in 1978 as a not-for-profit organization to induce compliance with the U.S. Copyright law.
CCC, based in Danvers, MA, provides licensing systems for reproduction and distribution of copyrighted materials throughout the world. Circular 66 from the U.
Copyright Office explains. Most of the material in this definition/topic was reprinted from an EditPros newsletter with their permission. EditPros is a writing, editing, and publishing management firm in Davis, California with their own. Cowboy Coding Posted by Cowboy coding describes an undisciplined approach to software development that allows individual programmers to make up their own rules. Cowboy coding is programming lingo for an approach to that gives programmers almost complete control over the development process. In this context, cowboy is a synonym for maverick -- an independent rebel who makes his own rules. An organization might permit cowboy coding because there are not enough resources to commit to the design phase or a project deadline is looming. Sometimes cowboy coding is permitted because of a misguided attempt to stimulate innovation or because communication channels fail and there is little or no business stakeholder involvement or managerial oversight.
An individual developer or small team might be given only a minimal description of requirements and no guidance regarding how these objectives should be achieved. They are free to select, coding languages,, technologies and other as they see fit. The cowboy approach to coding typically focuses on quick fixes and getting a working product into production as quickly as possible.
There is no or formal process for testing, as required by and other methodologies. Instead of producing lean, well-written code, cowboy code often has errors that cause failures upon deployment or make it difficult to maintain over time. Integrating the various components of the code may also be a challenge since with cowboy coding there are no agreed-upon to provide continuity.
Continue Reading About cowboy coding • • • • • • • L • Link. Creating and Testing Your IT Recovery Plan Regular tests of your IT disaster recovery plan can mean the difference between a temporary inconvenience or going out of business. Testing at least once per month is important to maintain engineering best practices, to comply with stringent standards for data protection and recovery, and to gain confidence and peace of mind. In the midst of disaster is not the time to determine the flaws in your backup and recovery system. Backup alone is useless without the ability to efficiently recover, and technologists know all too well that the only path from “ought to work” to “known to work” is through testing.
A recent study found that only 16 percent of companies test their disaster recovery plan each month, with over half testing just once or twice per year, if ever. Adding to the concern, almost one – third of tests resulted in failure. The reasons cited for infrequent testing include the usual litany of tight budgets, disruption to employees and customers, interruption of sales and revenue, and of course the scarcity of time. This survey covered mostly large enterprises, and the challenges are even greater for smaller firms. According to the survey findings1, half of the SMBs that have implemented disaster preparedness plans did so after experiencing an outage and/or data loss. Fifty –two percent put together their plans with in the last six months. However, only 28percent have actually tested their recovery plans. Yet new systems have arrived that allow daily automated testing of full recovery, putting such assurances in reach of every business.
Backup without rapid recovery and testing will soon be as obsolete as buildings without sprinklers or cars without seatbelts. Please read the attached whitepaper.
Not Creating a Disaster Recovery Plan Could Cost You Everything by Disaster recovery planning is a very large topic, with just one part being about backing up and recovering your data. To give you a real life example of what I mean by saying that data backup and recovery is just part of an overall disaster recovery plan, I will refer to a. The post talks about how the System Admin gets a ticket saying that the power is out in their office in Kiev and that the UPS battery is down to 13%.
In response, the technician at the office simply shuts down the gear. The next day they received a news report that basically stated that the entire building, that was once their Kiev office, was no longer functional as fire and collapsed floors had completely devastated it. The System Admin ends his post by asking how is your disaster recovery plan, and have you tested it. When you start thinking about planning out your disaster recovery plan, you need to think about completely unrealistic disasters, along with the normal types of disaster crisis scenarios. If you have a disaster recovery plan already in place, does it take into account what happens if the office is completely destroyed or is inaccessible?
How about multiple points of connectivity? When was the last time that your disaster recovery plan was actually tested? When to Test Your Disaster Recovery Plan It is a good practice to update and test your disaster recovery plan whenever large changes are made. What happens when you have everything set the way you want it and nothing huge has changed? My suggestion is to treat it like your smoke detector; twice a year when the time changes and you change the batteries in your smoke detectors, test your entire disaster recovery plan.
Testing that plan should include asking yourself questions and exploring “what if” scenarios like: what happens if Bob, the main System Admin goes missing or dies by the proverbial bus that hunts down System Admins, or what happens if the building is on fire and everything inside is gone, or what happens if the cloud service you rely on for production/backup/disaster recovery suddenly closes its doors. All of these things needs to be accounted for along with many other scenarios in order to be able to recover from a disaster and continue running your business. Not Making Time for Disaster Recovery Could Cost You It seems like one of the hardest things to do is to make the time to either create or test your disaster recovery plan. Most of the time it seems like it comes down to time, and not having enough time is the biggest excuse given for not creating or testing a disaster recovery plan. This issue of time almost always comes down to priorities. When creating or testing your disaster recovery plan is too low on your priority list, it simply never gets done.
One of the best ways to go about pushing up the priority of disaster recovery is simply to think about how much each minute, hour, day, and week of downtime will cost the company. For instance, say an hour of downtime on the company website costs the company $3000 in lost e-commerce revenue. Now multiply that over hours or even days and your talking about huge potential losses that could have been avoided.
Plus, that is not even factoring in the potential revenue loss of new customers who may not even consider your company after not being able to read about your company/products or the negative affect it has on the company image. The costs, even in this small scale disaster scenery, add up quickly. The reality is, if you think data loss won’t happen to your company think again. 74% of companies have experienced at the workplace and 32% of companies take several days to recover from the loss of data. The scary truth is 16% of companies that experience data loss never recover. When you think in terms of the potential cost to the company, it should help you prioritize your disaster recovery planning and testing along with justifying the costs of both the planning, infrastructure, and testing.
I think Benjamin Franklin said it best when he stated “If you fail to plan, you plan to fail.” When it comes to disaster recovery, failing to have a plan is a sure-fire way to set the company up for failure in the event of a disaster, and it could cost the company everything. If you liked this post, Link.
Creative Commons is a nonprofit organization that offers licenses for digital work. No registration is necessary to use the Creative Commons licenses. Instead, content creators select which of the organization's six licenses best meets their goals, then tag their work so that others know under which terms and conditions the work is released. Users can search the CreativeCommons.org website for creative works such as music, videos, academic writing, or to use commercially or to modify, adapt or build upon. The six categories of licenses offered are: • Attribution - lets others distribute, remix, tweak and build upon work, even commercially, as long as they credit the creator for the original work. • Attribution-NoDerivs - allows for commercial and non-commercial redistribution, as long as the work is passed along unchanged and in whole, crediting the creator. • Attribution-NonCommercial-ShareAlike - lets others remix, tweak, and build upon work for non-commercial purposes, as long as they credit the creator and license any new creations under the identical terms. • Attribution-ShareAlike - lets others remix, tweak, and build upon work for commercial and non-commercial purposes, as long as they credit the creator and license new creations under the identical terms.
• Attribution-NonCommercial - lets others remix, tweak, and build upon work for non-commercial purposes, crediting the creator. Derivative works do not have to be licensed under the same terms. • Attribution-NonCommercial-NoDerivs - allows others to download work and share it as long as they credit the creator, don't change the work in any way or use it for commercial purposes. See also:, This was last updated in July 2013. 10 KEY QUESTIONS (AND ANSWERS) ON CROWDSOURCING FOR ENTERPRISE IT A starting guide for augmenting technical teams with crowdsourced design, development and data science talent A crowdsourcing platform is essentially an open marketplace for technical talent.
The requirements, timelines, and economics behind crowdsourced projects are critical to successful outcomes. Varying crowdsourcing communities have an equal variety of payments being offered for open innovation challenges. Crowdsourcing is meritocratic - contributions are rewarded based on value. However, the cost-efficiencies of a crowdsourced model reside in the model's direct access to talent, not in the compensated value for that talent.
Fair market value is expected for any work output. The major cost difference with between legacy sourcing models and a crowdsourcing model is (1) the ability to directly tap into technical expertise, and (2) that costs are NOT based around time or effort.
Please read the attached whitepaper. Mastering the Modern Customer Service Model by Wheelhouse Enterprises Perfecting your in-house customer service system has never been easy until now. The cloud has made customer service tools readily available and revolutionized how they are implemented.
Our newest white paper details the tools necessary for the most modern, up-to-date customer service tools for your organization. Whether you're looking for specific tools for your contact center or CRM, we have you covered. Please read the attached whitepaper.
• - A data center (sometimes spelled datacenter) is a centr. • - A data center as a service (D. • - A data center. • - Data center bridging (DCB) describes. • - Data center bridging (DCB. • - A data center chiller is a cooling syst. • - Evaporative coo.
• • - A data center in a box, also called a. • • - We've gathered a collec. • - DCML (Data Center Marku.
• - We've gathered a collection of our quiz. • - Data center resiliency is the abi. • - Data protection managemen. • - Data protecti. • - A data center as a service (DCaaS) provider will supply turnkey phy. • - Data center bridging (DCB) describes the four technology enhancements t.
• - Data center infrastructure efficiency (DCIE) is a metric used to dete. • - Data center infrastructure management (DCIM) is the convergence of IT. • - Demand signal repository (DSR. • - Demand signal rep. • - Electrical pollution is electromagnetic-fie.
• - Disaster recovery is the area of security p. • • - Desktop Management Interface (DMI) is an industry framework for managin. • - Desktop M. • - Data protection management (DPM) is the administration of backup proces. • - Demand signal repository (DSR) is a database that aggregates sales data. • - D is one of two programming languages, Digital Mars D, an object-oriented m.
• - D-AMPS (Digital-Advanced Mobile Phone Service), sometimes spelled. • - D-VHS (Digital Video Home System) is a digital enhancement of the V. • - D-AMPS (Digital-Advanced Mobile Phone Service), sometimes spelled. • • - In the Integrated Services Digital Network (ISDN), the D-ch.
• - D-VHS (Digital Video Home System) is a digital enhancement of the V. • - D-VHS (Digi. • - D2D2C (disk-to-disk-to-cloud) is an approach to hybrid cloud backup. • - D2D2C (disk-to-disk.
• - Disk-to-disk-to-tape (D2D2T) is an approach to computer storage bac. • - Data analytics (DA) is the science of examining raw data with the purpose. • - A Data Access Arrangement (DAA) is an electronic interface within a com. • - Desktop as a service (DaaS), also called virtual desktop or hosted de. • - Digital audio broadcasting (DAB), also known as digital radio and high. • - Digital-to-analog conversion is a process in which signals having a few.
• - A daemon (pronounced DEE-muhn) is a program that runs continuousl. • - Direct Access File System (DAFS) is a network file system, similar to. • - Smoke testing is non-exha. • - A daily stand-up meeting is a sho. • - A daisy chain is an interconnection of computer devices. • - Database activity monitoring (DAM) systems monitor and record activity.
• - DAML (DARPA Agent Markup Language) is a markup language for the U.S. • - DAML (DAR. • - Skinny Linux is an umbrella term that encompa. • - D-AMPS (Digital-Advanced Mobile Phone Service), sometimes spelled D. • - DAO (Data Access Objects) is an application program interface (API) ava.
• - DAO (Data Access Objects) i. • - The Defense Acquisition Regulatory Council (DARC) is a group composed. • - A dark backup is one that can be run automatically with.
• - Dark energy, also called quintessence, is a mysterious. • - Dark energy, also called. • - Dark fiber is optical fiber infrastructure (cabling and r. • - A darknet is a routed allocation of IP address space that is no. • - DARPA (Defense Advanced Research Projects Agency) is the independen. • • - DAML (DARPA Agent Marku. • - DARPANET (or DARPANet) is a term sometimes used for the ARPAN.
• - Darwin is the basic 'core' of OS X, the operating system for Appl. • - Direct-attached storage (DAS) is computer storage that is directly atta. • - A distributed antenna system (DAS) is a way to efficiently distribute w. • - Direct access storage device (DASD, pronounced DAZ-dee), is a general. • - In information technology, a dashboard is a user interface. • - Data visualization is a graphical representation of numer. • - DAT (Digital Audio Tape) is a standard medium and technology for the di.
• - DAT (Digital Audio Tape) is a. • - A DAT USB drive is a tape drive with digital audio. • - A DAT USB drive is a tape drive with digi. • - In computing, data is information that has been translated into a for.
• - A Data Access Arrangement (DAA). • - A Data Access Arran. • - DAO (Data Access Objects) is an applica. • - Data aggregation is any process in which info. • - Data mining is the analysis of data for relationshi. • - Data analytics (DA) is the science of examining r. • - Data analytics (DA) is the science of e.
• - Data archiving is the process of moving data that. • - Data as a Service (DaaS) is an information.
• - Data at rest is a term that is sometimes used to refe. • - Data availability is a term used by some co. • - Data binding is a process that allows an Internet use.
• - A data breach is an incident in which sensitive, protec. • - A data breach response plan. • - Data classification is the categorizati. • - A data center (sometimes spelled datacenter) is a centr. • - A data center as a service (D. • - A data center.
• - Data center bridging (DCB) describes. • - Data center bridging (DCB. • - A data center chiller is a cooling syst. • - Evaporative coo. • • - A data center in a box, also called a. • • - We've gathered a collec.
• - DCML (Data Center Marku. • - We've gathered a collection of our quiz. • - Data center resiliency is the abi. • - Data center services is a collective. • - Data classification is the categorizati. • - Data scrubbing, also called data cleansing, is th. • - In network computing.
• - Data corruption is the deterioration of compute. • - Data curation is the management of data throughout. • - A data encryption/decryption IC is a spec. • - Data deduplication (often called 'intelli. • • - Data Definition Language (DDL. • - Data Definition L.
• - A data dictionary is a collection of descriptio. • - Data dredging, sometimes referred to as data fishin. • - Data dredging, someti. • - A data encryption/decryption IC is a spec. • - Data Encryption Standard (DES.
• - Data Encryption S. • - A data encryption/d.
• - Data exfiltration, also called data extrusi. • - Data exfi. • - Data exfiltration, also called data extrusion, is. • - Data federation technology, a.
• - Data federation technolog. • • - In data processing, using an office metaphor, a file is a r. • - Data dredging, sometimes referred to as data fishing. • - A data glove is an interactive device, resembling a glove. • - Data governance (DG) refers to the overall mana. • - Data governance (DG) refers to the ov.
• - A data governance policy is an. • - Droupie (for data groupie) is computer jargon for som. • - Data hiding is a characteristic of object-oriented prog. • - Data hygiene is the collective processes conducted to.
• - Data ingestion is the process of obtaining, impor. • - Customer data integration (CDI) is the proces.
• - Integrity, in terms of data and network security. • - In cryptography, a data key is a key (a variable value that i. • - Data latency is the time it takes for data packets to. • - Data life cycle managemen. • - Data life cyc. • - Data life cycle management.
• - DLC also is an abbreviation for digital loo. • - DLC also is an abbreviation for. • - The Data-Link Layer is the protocol layer in a. • - Data loss prevention (DLP) is a strat. • - Data loss prevention (DLP.
• - Data management is the development and executio. • • - We've gathered. • - A data management. • - We've gathered a collection of. • - A data mart is a repository of data gathered from operation. • - A data mart is a repository of data g. • - An enterprise mashup is the integration of heterogeneou.
• - Data masking is a method of creating a structurally s. • - Data mining is the analysis of data for relationships tha.
• - Data mining is the analysis of data for relationships t. • - Data modeling is the analysis of data objects that. • • - Now known a.
• - The data plane (sometimes known as the user pla. • - A data point is a discrete unit of information.
• - Data portability is the ability to move data. • - Data preprocessing describes any type of. • - Consumer privacy, also known as customer privacy, inv. • - Data profiling is a set of algorithms for statist. • - Data protection managemen.
• - Data protecti. • - In computing, data quality is the reliability and app. • - In computing, data quality is the. • - The data transfer rate (DTR) is the amount of digital data.
• - Data recovery is the process of restoring data that. • - A data recovery agent (DRA) is a Micros.
• - A data recovery agent (DRA). • - Data reduction is the process of minimizing the a. • • - A storage replication service is a managed se. • - A knowledge warehouse is the component of an en. • - Data science is the study of where information comes. • - A data scientist is a job title for an employee o.
• - Data scrubbing, also called data cleansing, is th. • - Data scrubbing. • - The Data Security. • - A CSU/DSU (Channel Service Unit/Data Servic. • - In an IBM mainframe operating system, a data set is a named c.
• - A data silo is a repository of fixed data that an organizat. • - A data source name (DSN) is a data structure. • - A data source name (DSN) is a dat. • - A data source object (DSO) is a Microsoft. • - A data source object (DSO) is.
• - A data source object (DSO. • - Data sovereignty is the concept that informat. • - DSTP (Data Space Tran. • - Data splitting is an approach to protecting sensi. • - Data stewardship is the management and oversi. • - Data streaming is the transfer of data at a stead.
• - A data structure is a specialized format for orga. • - An ABCD data switch is a small box that lets you hook u. • - In computer data transmission. • - The data transfer rate (DTR) is the amoun.
• - The data transfer rate (DTR). • - Throttled data transfer, also. • - A data type in a programming language is a set of data with. • - Data virtualization is an umbrella term. • - Data federation t.
• - Data visualization is a general term used. • - Data visualization is a graphical represe. • • - A data warehouse appliance is. • • • - A data-driven disaster is a serious p. • - The Data-Link layer is the protocol layer in a.
• - A database is a collection of information that is organized s. • - Database activity mon. • - Database. • - (DBA is also an abbreviation for. • - (DBA is also an abbre. • - A cloud database is a database that. • - A database.
• - A cursor is the position indicator on a compute. • - This is a glossary for database terminology. • - We've gathered a collection o. • - A database management sys. • - A database. • - Database marketing is a systematic approa. • - Database mirroring is the maintenance of.
• - A database of record (DBOR) is a reposito. • - A database of record (DBOR). • - We've gathered a collection of our quizzes on. • - Database replication is the frequent.
• - Database-agnostic is a term describing the. • - This is a glossary of database-related te. • - A datacard is any removable computer component, approximately.
• - A datagram is, to quote the Internet's Request for Comments 1. • - A data mart is a repository of data gathered from operational. • - DataTAC is a narrowband wireless network that began as a joint. • - A daughterboard (or daughter board, daughter card. • - A daughterboard (or daughter board, daughter card. • - A daughterboard (or daughter board, daughter card. • • - A daughterboard (or daughter board, daughter card,.
• - A digital audio workstation (DAW) is a computer that is specially equip. • - Daylight Saving Time (DST) is the pra. • - Daylight Saving Time (DST. • - A Daylight Saving Time pa. • - Daylight Saving Time (DST) is the p.
• - In electronics and communications, the decibel (abbreviated as dB, and al. • - A-weighted decibels, abbreviated dBA, or dBa, or dB(a), are an expr. • - DB-xx is the designation for a series of port connectors for attach. • - DB-xx is the designation for a series of port connectors for attach. • - DB-xx is the designation for a series of port connectors for attach. • - DB-xx is the designation for a series of port connectors for attach. • - DB-xx is the designation for a series of port connectors for attachin.
• - DB-xx is the designation for a series of port connectors for attach. • • - DB2 is a family of relational database management system (RDBMS) produc. • - (DBA is also an abbreviation for doing business as - a term sometimes u. • - A-weighted decibels, abbreviated dBA, or dBa, or dB(a), are an expressi.
• - dBc (decibels relative to carrier) is a measure of the strength of an i. • - dBd (decibels related to dipole antenna) is a measure of the gain of an.
• - The expression dBi is used to define the gain of an antenna system rela. • - The expression dBm is used to define signal strength in wires and cable. • - A database management system (DBMS), sometimes just called a database. • - dBmV (decibels relative to one millivolt) is a measure of the signal.
• - A database of record (DBOR) is a repository for centralized storage o. • - The expression dBr is used to define signal strength at RF and AF frequ. • - Direct broadcast satellite (DBS) refers to satellite television (TV) sy. • - Demand-based switching (DBS) is a power-management technology developed. • - DC (direct current) is the unidirectional flow or movement of electric ch.
• - DC (direct current) is the unidirection. • - A data center as a service (DCaaS) provider will supply turnkey phy. • - Data center bridging (DCB) describes the four technology enhancements t. • - In network computing, DCE (Distributed Computing Environment) is an ind.
• • - Data center infrastructure efficiency (DCIE) is a metric used to dete. • - Data center infrastructure management (DCIM) is the convergence of IT. • - DCIT (Digital Compression of Increased Transmission) is an approach t.
• • - Dynamic case management (DCM) is the handling of case-based work throug. • - The Defense Contract Management Agency is the government agency that. • - DCML (Data Center Markup Language), based on Extensible Markup Langua. • - DCML (Dat. • - DCOM (Distributed Component Object Model) is a set of Microsoft conce.
• - A DDBMS (distributed database management system) is a centralized a. • • - Double-Density Compact Disk (DDCD) is a CD format that increases the. • - In the Windows, OS/2, and (with third-party development kits) other ope. • - A driver development kit (DDK) is a set of programs and related files t. • - Data Definition Language (DDL) is a standard for commands that define t.
• - Demand-driven manufacturing (DDM) is an approach to manufacturing where. • - Direct digital marketing (DDM) is the electronic delivery of relevant c. • - On the Internet, a distributed denial-of-service (DDoS) attack is one.
• - On the Internet, a distributed denial-of-service (DDoS). • - DDR SDRAM (double data rate SDRAM) is synchronous dynamic R.
• - DDR SDRAM. • - Digital Data Storage (DDS) is a format for storing and backing up compu. • - Digital Data Storage (DDS) is a format for storing and backing up c. • - Digital Data Storage (DDS) is a format for storing and backing up c. • - Digital Data Storage (DDS) is a format for storing and backing up c. • - Digital Data Storage (DDS) is a format for storing and backing up c. • - De-anonymization is a data mining strategy in.
• - De-anonymization is a data mining strategy in. • - De-anonym. • - In network security, deperimeterization. • - In network security, deperimeterization.
• - Dead body spam, also known as corpse graffiti, is. • - Dead body spa.
• - In 1995, science-fiction writer Bruce Sterling challenged. • - Debian is a popular and freely-available computer operating syste. • - Debian is a popular and freely-available computer ope.
• - Bouncing is the tendency of any two metal contacts in an el. • - Bouncing is the tendency of any two metal contacts in an. • - In computers, debugging is the process of locating and fixing. • - In computers, debugging is the process of locating and fixing. • - In computers, debugging is the process of locating and fixi. • - Now part of Compaq, DEC (Digital Equipment Corporation) has long occupi.
• - In electronics and communications, the decibel (abbreviated as. • - dBd (deci. • • - dBc (decibels relativ.
• - dBc (deci. • • • - dBmV (dec. • • - The expre. • • - Decimal is a term that describes the base-10 number system, pro. • - All three terms - decipher, decrypt, and decode - mean to con. • - Decision management is a process or set.
• - A decision support system (DSS). • - A decision support. • - A decision tree is a graph that uses a branching me. • - In data mining, decision tree sof. • - All three terms - decipher, decrypt, and decode - mean to convert. • - Encoding is the process of putting a sequence of characters (. • - To decompile is to convert executable (ready-to-run.
• - To decompile is to convert executable (ready-to-run) progra. • - To decompile is to convert executable (ready-to-run) prog. • - Uncompressing (or decompressing) is the act of expa. • - In general, a decoupled architect. • - All three terms - decipher, decrypt, and decode - mean to conve. • - Encryption is the conversion of data into a form, called.
• - Unlike the analog cordless phones you may have in your home, DECT (Di. • • - In the Web hosting business, a dedicated se. • - A dedicated line is a telecommunications path bet. • - In the Web hosting business, a dedicated serv. • - Deep analytics is the application of sophisticate.
• - A deep link is a hypertext link to a page on a Web site oth. • - Deep packet inspection (DPI) is a.
• - Deep packet inspectio. • - The Deep Space Network (DSN) is a sophist. • - The Deep Space Network (DSN). • - The deep Web is the part of the Internet that is inaccessible.
• - In computer technology, a default (noun, pronounced dee-FAWLT). • • • • • - The Defen.
• • - A defense contractor is any person who en. • - Defense in depth is the coordinated use of mu.
• - Defense I. • • - The Defense Message System (DMS).
• - The Defense Message S. • - Defragmentation is the process of locating the noncontiguous frag. • - Defragmentation is the process of locating the noncontigu.
• - Defragmentation is the process of locating the. • - A defragmenter is a software utility that rearranges.
• - The angular degree is a unit of plane angular measure used in some engi. • - To degauss is to demagnetize. The term is named after Carl Frie. • - The degree Fahrenheit (o F) is the unit of.
• - The degree per second is a unit of angular. • - The degree per second squar. • - Degrees of freedom, in a mechanics contex. • - A delay-tolerant network is a net. • - DelFly is a remotely controlled, camera-equipped, highly maneuver.
• - In computer programming, a delimiter is a character that id. • - Deliverable, as an adjective, describes something that. • • • - Dell Boomi is a Software as a Service (SaaS) integration. • - Delphi (pronounced DEHL-FAI) from Borland competes with Visual Ba. • - We've gathered cheat sheets for fast re. • - Delta differencing (also called 'delta di.
• • - Delta differencing (also called 'delta di. • - Demand-based switching (DBS) is a.
• - Demand-driven manufactu. • - A demand flow sched. • - Demand planning is a multi-step operational sup. • - Demand signal repository (DSR. • - Demand signal rep. • - Demand-based switching (DBS) is a.
• - Demand-based switchin. • - Demand-driven manufactu. • - Demand-driv. • - A demarc (an abbreviation for demarcation point) marks the point. • - A demarc (an abbreviation. • - A demarc (an abbreviation for demarcation p.
• - In computer networks, a DMZ (demilitarize. • - A demo is a non-interactive multimedia presentation that is rendered. • - A demo is a non-interactive multimedia pr. • - Demographics is the study of the behaviors and other. • - A demo is a non-interactive multimedia presentation that is. • - A demo is a non-interactive multimedia presentation that is. • - A demon (also see daemon which has a somewhat similar meaning) is a.
• - A demo is a non-interactive multimedia presentation that is. • - A demo is a non-interactive multimedia presentation that is. • - Demutualization is the process through which a. • - Directory-Enabled Networking (DEN) is an industry-standard initiative a. • - Directory. • - A dendrimer (from Greek dendra for tree) is an artificially. • - Deniable encryption is a type of crypto.
• - A denial of service (DoS) attack is an inci. • - A denial of service (DoS) attac. • - A denial of service (DoS) att. • - A denial of service (DoS) attack is an inci. • - A denial of service (DoS) att. • - In a relational database, denormalization is an.
• • • - Obfuscation, in general, describes a practice that is u. • - A dependent variable is a variable whose.
• - In network security, deperimeterization i. • - In network security, deperimeterization i. • - To deploy (from the French deployer) is 'to spread out or arrange. • - A depository is a file or set of files in which data is s. • - In dictionaries, deprecated is a term used to indicate a pr.
• - In dictionaries, deprecated is a term used to indicate a. • - In dictionaries, deprecated is a term used to indicate.
• - E-voting is an election system that allows a voter to record his or her. • - A derived object (DO) is a file created in a Vers.
• - A derived object (DO) is a file created. • - Data Encryption Standard (DES) is a widely-used method of data encrypti. • - Descriptive modeling is a mathematica. • - A SerDes or serializer/deserializer is an integrated. • - Design by committee is a term sometimes. • - In software development, a pattern (or design pat. • - In information technology, design reuse is the inclus.
• - Using an office metaphor, a desktop is a computer display area. • - Desktop management is a comprehen. • - Desktop as a service (DaaS), also cal.
• - Desktop as a service (D. • • - A desktop computer is a personal computer tha. • - A personal firewall (sometimes called a deskt. • - A desktop gadget is a software widget, or a small. • - Desktop layering is a method of dividing a di. • - Desktop management is a comprehensive app. • - Desktop Management In.
• - The Distributed Man. • - Desktop NAS (network-attached storage) is a device that. • - Desktop personalization is the. • - Desktop search (sometimes called integrated searc.
• - Desktop s. • - Desktop management is a comprehensive approac. • - A desktop supercomputer, also calle. • • - A desktop theme is a customized graphical user inte. • - Desktop virtualization is the con. • - Destreaming, in a multimedia context, is the practice o.
• - Destructive testing is a software asses. • - In computer program and softwar. • - DevOps is the blending of tasks p. • - DevOps is the blending of tasks p. • - Developmental robotics is the use.
• - In general, a device is a machine designed for a purpose. • - Device agnostic is a description for computing. • - Device agnostic is a description for comp.
• - A device attack is an exploit in which the attacker. • - A device driver is a program that controls a partic. • - A device ID. • - Device relationsh. • - Device agnostic is a description for computing.
• - DeviceCOM, from Intrinsyc Software, is a line of device and. • - DevOps is the blending of tasks performed by a company's applicat. • - DevOps is the b. • - A distributed file system is a client/server-based application that all. • - Data governance (DG) refers to the overall management of the availability. • - DGS&D is the central.
• - A directory harvest attack (DHA) is an attempt to determine the valid e. • - DHCP (Dynamic Host Configuration Protocol) is a communications protoc. • • - Dynamic HTML is a collective term for a combination of Hypertext Ma.
• - Double-parity RAID (redundant array o. • - A dial peer, also known as an addressable call endpoint, is.
• - Dial peer hunting is a feature of voice ove. • - Dial-up pertains to a telephone connection in a system of many. • - High-speed dialup, sometimes advertis. • • - A menu is a set of options presented to the user of a com. • - The famous diary that Samuel Pepys.
• - A binary search, also called a dichot. • - DICOM (Digital Imaging and Communications in Medicine) is an applic.
• • - Quick look-up for more tech. • - A dictionary attack is a method of breaking. • - Direct Inward Dialing (DID) is a service of a local phone company (or l. • - DidTheyReadIt is an e-mail nonrepudiation program t. • - A dielectric material is a substance that is a poor condu. • - The dielectric constant is the ratio of.
• - A dielectric material is a substance th. • - The Difference Engine, designed in the 1820. • - A differencing disk is a virtual hard disk. • - A differential backup is a type of back.
• - A differential power an. • - A different. • - A differe.
• - A differential power. • - Differentiated Services (DiffSe. • • - Diffie-Hellman key exch. • - Diffie-Hellman key exch. • • - Differentiated Services (DiffServ, or DS) is a protocol for s. • - Digest authentication is a method o.
• - Digg is a social news site that allows members to raise the visibilit. • - Digiboard or digicard is a generic name for a serial port c. • - Digiboard or digicard is a gene.
• - Digiboard or digicard is a generic name for a serial port car. • - A digit is an element of a set that, taken as a whole, comprises a. • - Digital describes electronic technology that generates, stores. • - Digital asset management (DAM.
• - Digital audio broadcastin. • - Digital audio. • - DAT (Digital Audio Tape) is a standard me.
• - A digital audio workstation. • - A digital audio. • - A digital camera records and stores photographic. • - Digital cash is a system of purchasing cash credits i. • - Digital cash is a system of purchasin. • - A digital certificate is an electronic. • • - Digital CRM is the use of multiple electronic communica.
• - In information technology, a dashboard is a. • - Digital Data Storage (DDS) is a forma. • • - Electronic discovery (also called e-discove. • - The term 'digital divide' describes the fact that. • - Dolly, also called Digital Dolly, is a program that.
• - Digital drugs, more accurately called binaural beat. • • - Digital enterprise is an organization tha. • - Now part of Compaq.
• - Electronic discovery (also called e-discovery. • - Electronic discovery (als. • - Ripping, more formally known as digital e. • - Digital film is any storage medium (such as a memory. • - A digital hearing aid is a hearing aid. • - D-VHS (Digital Video Home S.
• • - A digital library is a collection of documents. • - DLT (digital linear tape) is a form of. • - DLC also is an abbreviation for Data.
• - DLC also is an abbreviati. • - Digital Mars D is a programming language develope. • - The Digital M. • • - Digital multime. • - Digital Negative (DNG) is an imaging specific. • - Digital Negative (DNG) is an imag. • - A DOI (digital object ident.
• - A DOI (digital. • - A digital pen is a battery-operated writing instrument. • - A digital photo album is an application. • - Digital Powerline (DPL) technology provides. • - Digital Powerline (DPL) technol.
• - Digital printing is any print. • - Digital printing describes the process of trans. • - Digital printing describes the process of tra.
• - A digital p. • - A digital projector, also called a digital. • • - Ultra wideband (also known as UWB.
• - Digital audio broadcasting (DAB), also known as dig. • - Digital rights management (. • - Digital rights. • - Satellite new. • - Digital signage, also called dynamic signage, i. • - Digital sig.
• - Digital signal processing (. • - Digital signal. • - Digital signal X is a term for the series of. • - A digital signature (not to be confused wit. • • - The Electronic Sign.
• - Digital Signature Standar. • - Digital Signa. • - Digital Silhouettes is the trademarked. • - When talking about digi. • - Quick look-up for understanding.
• • • - A digital switch is a device that handles digital. • - Digital television (DTV) is the transmiss. • - Digital television (DTV) is t.
• - DTTV (digital ter. • - Digital Text Platform (DTP) is Amaz. • - Digital Text Platform (. • - Digital-to-analog con. • - DVD is an optical disc technology.
• - Digital video is audio/visual data in a binary form. • - Digital Video Broadcastin. • - Digital Video. • - DVD is an optical disc technology with a. • - No longer sold, Divx (Digital Video.
• - No longer sold, Divx. • - D-VHS (Digital Video Home S. • - DVI (Digital Visual Interface).
• - DVI (Digital Visual Interface. • - In general, a digital wallet is a software applic. • - A forensic watermark, also called a digital.
• - Digital-to-analog con. • - Digital-t.
• - D-VHS (Digital Video Home System) is a digital enhancem. • - Digitization is the process of converting information. • - Digitization is the process of converting information into a. • - A digitizer tablet (also known as a digitizer or graphics t. • - Digitizer software is the collection of p. • - A digitizer tablet (also known as a digitizer.
• • - Digitization is the process of converting information int. • - A digizine is a magazine that is delivered in digital (electr. • - Dilbert is a cartoon strip about the workplace that has a wide. • - DIME (Direct Internet Message Encapsulation) is a communications spec.
• • - In data warehousing, a dimension is a collection of referen. • - A dimension table is a table in a star schema o. • - A DIMM (dual in-line memory module) is a double SIMM (single in-line. • - A DIMM (dua. • - A diode is a specialized electronic component with two electrodes c. • - A laser diode, also known as an injection laser or diod.
• - A dipole antenna is a straight electrical conduct. • - In computer storage, direct access is the ability t. • - Direct Access File System (. • - Direct Access. • - Direct access storage. • - Direct-attached storage (DAS) i.
• - Direct broadcast satellit. • - Direct broadc. • - DC (direct current) is the unidirectional flow. • - Direct digital marketing (DDM. • - Direct digital ma. • - Direct email marketing is a forma.
• - Direct Inward Dialing (DID) is a se. • - Direct Inward Dialing (. • - A direct market reseller (DMR), a. • - A direct market resel. • - Direct marketing is a type of advertising cam. • - Direct Memory Access (DMA) is a capab.
• - Direct Memory Access (DMA. • - Direct mobile billing is a method o. • - Direct Outward Dialing (DOD) is a. • - Direct Outward Dialin. • - Direct R/3 is a partnership program between Dell Computer.
• - RDRAM (Rambus Dynamic Random Access Memory) is a me. • • - Direct sequence. • • - Reverse Telnet (sometimes called direct Telnet) is. • - Direct-to-Edit (DTE) is a video recording technol. • - Direct-attached storage (DAS) i. • - Direct-attached sto. • - Direct-to-Edit (DTE) is a video recording technol.
• - Direct-to-Edit (DTE) is a video recor. • - Direct broadcast satellite (D. • - DirectAccess is a feature introduced in Windows Serve.
• - A directional antenna is a radio-freque. • - Directional sound is a technology that conc. • - EU Data Protection Directive (also known. • - Director of First I. • - A directory is, in general, an approach to organizing infor. • - Directory traversal is a form of HTTP exp.
• - Directory-Enabled Net. • - A directory harvest attack (D.
• - A directory harve. • - DSML (Dir. • • - Directory traversal is a form of HTTP e. • - Directory-Enabled Net. • - DirectX is an application program interface (API) for creating.
• - In a data warehouse, dirty data is a database record that. • - Electrical pollution is electromagnetic-fie. • - DirXML is Novell's directory interchange software that uses XML t. • - Defense Information Systems Agency (DISA) is a U.S combat support age.
• - Disambiguation (also called word sense disambigua. • - Disappearing e-mail is a message sent u. • - In programming terminology, to disassemble is to conver. • - In programming terminology, to disassemble is to conv.
• - A disaster recovery plan (DRP) -- sometimes. • - Disaster recovery is the area of security p. • - A disaster recovery (DR.
• • - A disaster recovery plan (DRP) -. • - A disaster recovery p. • - A disaster recovery plan. • - Discontinuous transmissio. • - Discontinuous. • - Discoverability is the capacity of something to.
• - Discoverability marketing i. • - Discrete (pronounced dihs-KREET, from the Latin discretus and. • - Discrete event. • - Discrete manufacturing is an indu. • - Discrete multitone (DMT) is a method of s. • - Discrete multitone (DMT) is a.
• - A discussion board (known also by various oth. • • - A discussion board (known also by various oth. • - A dish antenna, also known simply as a dish, is commo. • - Disintermediation is giving the user or the. • - Disjoint namespace is an occurrence in Ac. • - A disk cache is a mechanism for improving the time it tak. • - Disk cloning is the act of copying the contents of a.
• - Disk duplexing is a variation of disk mirroring i. • - A disk image is a copy of the entire contents of a storag. • - Disk duplexing is a variation of disk mirroring i. • - Disk mirroring, also known as RAID 1, is the repl. • - Disk mirroring, also known as R.
• - DOS (Disk Operating System) was the. • - Diskpart is a command-line utilit. • - In computers that use multiple hard disk systems, d. • - D2D2C (disk-to-disk-to-cloud) is an. • - Disk-to-disk-to-tape (D2D2T) is an ap. • - D2D2C (disk-to-disk-to-cloud) is an.
• - Disk-to-disk-to-tape (D2D2T) is an ap. • - Disk-to-disk-to-tape. • - A diskette is a random access, removable data storage medium. • - A diskette is a random access, re. • - A USB drive -- also known as a flash drive or keychain driv. • - Diskpart is a command-line utility used to manipulate disk pa.
• - Diskpart is. • - Running disparity (RD or rd) is the difference between the. • - Displacement (symbolized d or s), also called length. • - A display is a computer output surface and projecting mechanism.
• - A video adapter (alternate terms include graphi. • - The term display mode refers to the characteristics o. • - The term display mode refers to the characteristics. • - A readerboard is a visual display board that conveys. • - DisplayPort is an interface for digital displays, parti.
• - This glossary of common terms related t. • - A disposable computer is a small data p. • - What is a disposable email?Disposable email i. • - A disposable PC is a relatively inexpensive but ful. • - A disruption-tolerant n. • - A disruption-tolerant n.
• - A disruptio. • - Disruptive innovation is the introd. • - Disruptive technology is a term coi. • - Displacement (symbolized d or s), also called length or dista.
• - Distance learning, sometimes called e-learn. • - Distance learning. • • - Computing is said to be 'distributed' when the computer. • - A distributed antenna sys.
• - A distributed. • - WebDAV (World Wide Web Distributed. • - DCOM (Dis. • - In general, distributed computing i.
• - In network. • • - A distributed database is a database. • • - On the Internet, a distributed de. • - A distributed file system is a. • - A distributed file.
• • - Distributed learning is a general ter. • - The Distrib. • • - DRBD (D. • - VMware DRS (Distr. • - Distributed search is a search engine mod. • - A distributed virtual swi. • - In marketing, distribution is the process of moving a.
• - A distribution channel is the network. • - In e-mail applications, a distribution list. • - Distributive nume. • - A distributor is an intermediary entity between a the p. • • - In marketing, distribution is the process of moving a product fro. • - Dithering is the attempt by a computer program to approximate a c. • - Dithering is the attempt by a computer program to approximate.
• - Dithering is the attempt by a computer program to approxima. • - The division sign resembles a dash or double dash w.
• - No longer sold, Divx (Digital Video Express) was a video movie rental. • - In creating a database, normalization is the process of organizing it. • - DLC also is an abbreviation for digital loop carrier. • - DLC also is an abbreviation for Data Link Control. • - A dynamic link library (DLL) is a collection of small programs, any of. • - Data life cycle management (DLM) is a policy-based approach to managing.
• - Data loss prevention (DLP) is a strategy for making sure that end users. • - DLT (digital linear tape) is a form of magnetic tape and drive system u.
• - DLT (digital linear tape) i. • - Direct Memory Access (DMA) is a capability provided by some computer bu. • - DMADV is a process defined by Motorola as part of their Six Sigma m. • • - Digital multimedia broadcasting (DMB) is the process of multicasting.
• - The Digital Millennium Copyright Act (DMCA) is a controversial United. • - Desktop Management Interface (DMI) is an industry framework for managin.
• - Desktop M. • - The Open Directory Project (ODP) is a human-edited index of Web sites. • - Dynamic multi-pathing (DMP) is a type of communication path control sof. • - Digital rights management (DRM) is a systematic approach to copyright p. • - A direct market reseller (DMR), also known as an e-tailer, is a company. • - The Defense Message System (DMS) is a secure X.400-based e-mail system.
• - Discrete multitone (DMT) is a method of separating a Digital Subscriber. • - The Distributed Management Task Force, Inc. (DMTF) is an organization. • - A dynamic multipoint virtual private network (DMVPN) is a secure ne. • - In computer networks, a DMZ (demilitarized zone) is a computer host. • - In computer networks, a DMZ (. • - (In chemistry, DNA stands for deoxyribonucleic acid.
• - DNA storage is the process of encoding and decoding bin. • - Distributive numerical control (DNC) is a technology that allows a sing. • - Digital Negative (DNG) is an imaging specification that provides for lo.
• - DNIS (Dialed Number Identification Service) is a telephone service th. • - The domain name system (DNS) is the way that Internet domain names are. • - Cache poisoning, also called domain nam. • - Cache poisoning, also called domain name system (DN. • - DNS rebinding is an exploit in which. • - DNS redirection is the controversial practice o. • - DNS Security Extensions (DNSSEC.
• - DNS Security. • - DNS Security Extensions (DNSSEC) are a set of Internet Engineerin. • - A derived object (DO) is a file created in a Versioned Object Base (VOB). • - The 'do not call' list is a registry of phone.
• - The 'do not call' list is a registry. • - Do Not Track (DNT) is a browser setting t. • • • - A quiz about information technology. • • • - In-house marketing is any mar. • - In the Apple OS X operating system, the dock is a user-modifiable row. • - A docking station is a hardware frame and set o. • - DoCoMo, also known as NTT DoCoMo, is a Japanese communications co.
• - DoCoMo, also known as NTT DoCoMo, is a. • - DoPa (DoCoMo Packet Trans. • - Now known as CableLabs Certified Cable Modems, DOCSIS (Data Over. • • - In general, a document (noun) is a record or the capturing of. • - Document capture is any one of several proces. • - EDM (Electronic Document Management) is.
• - Document Object Model (DOM), a prog. • - Document Object Model (.
• - A document reader is a device that converts an. • • - A Document Type Definition (D. • - A Document Type D. • - In computer hardware and software product developme.
• - Direct Outward Dialing (DOD) is a service of a local phone company (or. • - The Dodd-Frank Act (fully known as the Dodd-Frank. • - The dogcow is a drawing of a rather indiscriminate-looking animal. • - Dogfood is an expression that means to use the product or servi. • - A DOI (digital object identifier) is a permanent identifier given to a.
• - Dolby Digital, formerly known as AC-3, is a digital. • - AC-3, also known as Dolby Digital, is a perceptual.
• - Dolly, also called Digital Dolly, is a program that can quickly clo. • - Dolly, also called Digital Dolly, i. • - Dolly, also called Digital Dolly, is a program.
• - Dolphin ArchiveLink Enabler (ALE) is an SAP ABAP add-on. • - Domino Off-Line Services (DOLS) is an add-on toolkit, based on Domino. • - Document Object Model (DOM), a programming interface specification bein.
• - In general, a domain is an area of control or a sphere of knowledge. • - Primary domain controller (PDC) and backup. • - Domain kiting is the practice of repeatedly registe.
• - In agile software development, a domain model describ. • - A domain name locates an organization or other entity o. • - The domain name system (DNS) is the way t. • - The domain name system (DNS). • - Cache poisoning, also. • - Domain rotation is a technique use by malware d. • - A domain sniper is a person or company that locates.
• - Domain tasting is the practice of purchasing nume. • - DomainKeys is an anti-spam software application in develo. • - Onshore outsourcing (also called dome. • - Domino is the name of the applications and messaging server progr. • - DXL (Domino Extensible La. • - Domino Off-Line Services (DOL. • - Domino Off-Line Services (DOL.
• - Domino Off-Line. • - A dongle (pronounced DONG-uhl) is a mechanism for ensuring that o. • - DoPa (DoCoMo Packet Transmission) is a packet-switched network servic. • - DoPa (DoCoM. • - The frequency and wavelength of an electromagneti. • - DOS (Disk Operating System) was the first widely-installed operating sy.
• - A denial of service (DoS) attack is an incident in which a user or orga. • - DOS (Disk Operating Sys. • - Although you may not use it on a daily basis.
• - DPMI (DOS Protected M. • - DOS/V is a version of MS-DOS that provides both. • - Dossia is a Web-based framework for storing and managing personal. • - Tip:To find out the dot address (such as 205.245.172.72. • - A dotcom is any Web site intended for business use and, in some. • -.NET is both a business strategy from Microsoft and its collect.
• - The dot pitch specification for a display monitor tells you. • - The dot product, also called the scalar product, of two. • - The dot product, also. • - Dot-green is a shorthand way of describing the green comput.
• - A dotcom is any Web site intended for business use and, in some. • - DOT4 is a protocol that allows a device that is part of a multifuncti.
• - A dotcom is any Web site intended for business use and, in some u. • - Test yourself. A WhatIs.com tech vocabulary quiz -p. • - In computers, dots per inch (dpi) is a measure of t. • - In computers, dots per inch (dpi) is a. • - Tip:To find out the dot address (such as 205.245.172.72. • - DDR SDRAM (double data rate SDRAM.
• • - Double-Density Compact Disk (DDCD) is a CD. • - Double-Density Compact.
• - The double factorial, symbolized by two excla. • - The double integral sign is used to i.
• - Double-Density Compact. • - Double-De. • - Double-parity RAID (redundant array of in. • - The double-slit experiment is a n.
• - A doubler is an electronic device that doubles the frequency of. • - Googlewhacking is the challenging pursuit of searching. • - IBM Dove (Distributed Overlay Virtual Ethernet). • - An HD (high-definition) downconverter is a device.
• - An HD (high-definition) downconverter is a device t. • - Downcycling is a recycling practice that involves break.
• - These terms should not be confused with downstream and upstream. • - These terms should not be confused with. • - Downloading is the transmission of a file from one computer s.
• - A pop-up download (sometimes called a download. • - A pop-up download (sometimes called a download. • - Downloading is the transmission of a file from one comp.
• - In a business enterprise, downsizing is reducing the numb. • - This term should not be confused with downlink. • - Uptime is a computer industry term for the time during which. • - A differential power analysis (DPA) attack is an exploit based on analy. • - The Data Protection Act 1998 (DPA 1998) is an act of the Unit. • - A differential power analysis (DPA) attack is an exploit based on ana. • - In computers, dots per inch (dpi) is a measure of the sharpness (that i.
• - Deep packet inspection (DPI) is an advanced method of packet filtering. • - Digital Powerline (DPL) technology provides the transmission of data to.
• - Data protection management (DPM) is the administration of backup proces. • - DPMI (DOS Protected Mode Interface) is a program interface that allow. • - In computing, data quality is the reliability and application efficienc. • - A data recovery agent (DRA) is a Microsoft Windows user who has been gr. • - A working draft (sometimes called a draft documen. • - Dynamic random access memory (DRAM) is the most common kind of random.
• - DRBD (Distributed Replicated Block Device) is a Linux-based software. • • - RDRAM (Rambus Dynamic Random Access Memory) is a memory subsystem. • • - As currently used in information technology, to drill down.
• - A drive-by download is a program that is au. • - Drive-by pharming is a vulnerability exploi. • - Drive-by spamming is a variation of drive-b. • - A drive-by download is a program that is auto. • - A driver is a program that interacts with a particular device. • - A driver development kit (DDK) is. • - A driver development.
• - A driverless car (sometimes called a self-driving. • - Drizzle is a lightweight open source database management system.
• - Digital rights management (DRM) is a systematic approach to copyright p. • - Device relationship management (DRM) is enterprise software that enable.
• - A backup robot is an automated external USB storage device that sup. • - DROP (delivery of real-time execution information protocol) is a feat. • • - In graphic design, a drop shadow is an effect where an. • - A menu is a set of options presented to the user. • - Dropbox is a cloud storage provider (sometimes referred to as a. • - A dropout is a small loss of data in an audio or video file on. • - Droupie (for data groupie) is computer jargon for someone who l.
• - Droupie (for data groupie) is com. • - A disaster recovery plan (DRP) -- sometimes referred to as a business c. • - Storage Distributed Resource Scheduler (DRS) is a feature of VMware’s v. • - Drupal is free, open source software that can be used by individu. • - Differentiated Services (DiffServ, or DS) is a protocol for specifying an.
• - Digital signal X is a ter. • - Direct sequence spread spectrum, also known as direct sequence. • - Digital signal X is a term for the series of standard digital transmiss. • - Digital signal X is a term for the series of standard digital transmiss. • - Digital signal X is a term for the series of standard digital transmiss. • - Digital signal X is a term for the series of standard digital transmiss.
• - Digital signal X is a term for the series of standard digital transmiss. • - The Data Security Council of India (DSCI) is a not-for-profit organiz. • - This is glossary of DSL (Digital Subscriber Line) t.
• - A DSLAM (Digital Subscriber Line Access Multiplexer) is a network d. • • - When talking about digital cameras, DSLR means digital. • • - DSML (Directory Services Markup Language) is an application of the Ex. • • - A data source name (DSN) is a data structure that contains the informat. • - The Deep Space Network (DSN) is a sophisticateddata communications syst. • - Satellite news gathering (SNG) is the use of mobile communications eq.
• - A data source object (DSO) is a Microsoft ActiveX object embedded withi. • - A data source object (DSO) exploit is a form of spyware. • • - Digital signal processing (DSP) refers to various techniques for improv. • - Dynamic Source Routing (DSR) is a self-maintaining routing protocol for. • - Demand signal repository (DSR) is a database that aggregates sales data. • - RFID (radio frequency identification) is a technology that incorporat.
• - Digital Signature Standard (DSS) is the digital signature algorithm(DSA. • - A decision support system (DSS) is a computer program application that. • - Direct sequence spread spectrum, also known as direct sequence code d. • - DSSSL (Document Style Semantics and Specification Language) is a st. • • - Daylight Saving Time (DST) is the practice of turning the clock ahead a.
• - A Daylight Saving Time patch is a modular piece of code cre. • - DSTP (Data Space Transfer Protocol) is a protocol that is used to ind. • - A CSU/DSU (Channel Service Unit/Data Service Unit) is a hardware device.
• - ISO/IEC 17799: Code of Practice for Inf. • - A Document Type Definition (DTD) is a specific document defining and co. • - In computer data transmission, DTE (Data Terminal Equipment) is the RS. • - Direct-to-Edit (DTE) is a video recording technology that converts the. • - In computer data tr. • - Direct broadcast satellite (DBS) refers to satellite television (TV) sy. • - DTMF (dual tone multi frequency) is the signal to the phone company t.
• - DTMF (dual to. • - A disruption-tolerant network (DTN) is a network designed so that tempo. • - Digital Text Platform (DTP) is Amazon.com's self-publishing service.
• - The data transfer rate (DTR) is the amount of digital data that is move. • - DTTV (digital terrestrial television, sometimes also abbreviated DTT). • - Digital television (DTV) is the transmission of television signals usin.
• - An HD (high-definition) upconverter, also kno. • - An HD (high-definition) upconverter, also known. • - Discontinuous transmission (DTX) is a method of momentarily powering-do. • - A dual boot system is a computer system in which two operat.
• - A multi-core processor is an integrated circuit (IC) to whi. • - A multi-core processor is an integrat. • - A multi-core processor is an integrated. • - A DIMM (dual in-line memo. • - A DIMM (dual in-line memo. • - Dual-layer magnetic tape, als.
• • - Dual-layer magnetic tape, also. • - DTMF (dual tone multi frequ. • - A dual Wi-Fi antenna is a pair of identic. • - Dual-layer magnetic tape, als. • • - Dual-layer magnetic tape, also. • - Dublin Core is an initiative to create a digital 'libra. • - In-house marketing is any marketing ini.
• - Due diligence is the process of systematically rese. • - In general, duh (pronounced DUH, prolonging the UH, pitching the voice. • - A dumb network is one that provides the physical interconnection betw.
• - A dumb network is one that provides the physical inte. • - In data communications, a terminal is any device th. • - A topsite is a stringently protected underground FTP server. • - Dumpster diving is looking for treasure in some. • - In graphic design, a duotone is an image composed of two colors. • - In telecommunication, duplex communication means that both ends o. • - Duqu is a remote access Trojan (RAT) that is designed to steal data f.
• - Duqu is a remote access Trojan (RAT) that is de. • - ACID (atomicity, consistency, isolation, and durability). • - Duty cycle is the proportion of time during which a compo. • - Digital Video Broadcasting (DVB) is a set of standards that define digi. • - DVD is an optical disc technology with a 4.7 gigabyte storage capacity. • - DVD is an optical disc techno. • - DVD-Audio (DVD-A) is a Digital Versatile Disc (DVD) format, develop.
• - DVD-Audio (DVD-A) is a Digital Versatile Disc (DVD) format. • - The DVD Forum is an international organization made up of c. • - DVD-Audio (DVD-A) is a Digital Versatile Disc (DVD) format, develop. • - DVD-Audio (DVD-A) is a Digital Versatile Disc (DVD) format. • - DVD-Audio (DVD-A) is a Digital Versatile Di. • - DVD-Audio (DVD-A) is a Digital Versatile Disc (DVD) forma.
• - DVD-RAM is a DVD(optical disc) technology for high-capacity dat. • - DVI (Digital Visual Interface) is a specification created by the Digita. • - DVI (Digital Visu. • - DVMRP (Distance Vector Multicast Routing Protocol) is the oldest ro. • • - The Dvorak (pronounced duh-VOR-ak, not like the. • - Dense wavelength division multiplexing (DWDM) is a technology that pu.
• - DXL (Domino Extensible Language) is a specific version of Extensible Ma. • - DXL (Domino E. • - Dynalink, a contraction for ' dynamic link library ' (DLL), i. • - In general, dynamic means energetic, capable of action and/or c. • - Dynamic analysis is the testing and evaluatio. • - In general, dynamic means energetic, capa.
• - A hot backup, also called a dynamic backup, is a. • - Dynamic business process management (BPM) is an approac. • • - Dynamic. • - Dynamic case management (DCM) i. • - Dynamic case manage. • - In the Windows, OS/2, and (with thi. • - In the Windows, OS/2, a.
• - A dynamic DNS (domain name system) serv. • - Dynamic fonts are a feature of Netscape's Communica. • - Lazy loading, also known as d.
• - Dynamic HTML is a collective term for a combination o. • - A static IP address is a number (in the f. • - In voice over IP (VoIP), a jitter b. • - A dynamic link library (DLL) is a col. • - A dynamic link library (D. • - Dynamic multi-pathing (DMP) is a ty.
• - Dynamic multi-pathing (DMP) is a ty. • - Dynamic multi-pathing (. • - A dynamic multipoint virtual priv. • - A dynamic multipo. • - A dynamic packet filter is a firewa. • - The dynamic port numbers (also known. • • - Dynamic random access.
• - Dynamic range describes the ratio of the softest so. • - Digital signage, also called dynamic signage, i. • - Dynamic Source Routing (DSR) is a. • - Dynamic Source Routin.
• - Dynamic SQL is an enhanced form of Structured Query Lan. • • - Dynamic SQL. • - Dynamic testing is a method of assessing the fe. • - A dynamic URL is the address - or Uniform Resource Loca. • - The dyne (dyn) is the centimeter-gram-second (cgs) unit of force.
• - Mergers and acqui. • • - A sea change is a significant and/or systemic transformat. • - Darwin is the basic 'core' of OS X, the operating system for Appl. • - Database-agnostic is a term describing the. • - Debian is a popular and freely-available computer operating syste. • - Debian is a popular and freely-available computer ope.
• - The Open Directory Project (ODP) is a human-edited index of Web sites. • - DRBD (Distributed Replicated Block Device) is a Linux-based software.
• • - Drizzle is a lightweight open source database management system. • - Drupal is free, open source software that can be used by individu. • - D2D2C (disk-to-disk-to-cloud) is an approach to hybrid cloud backup. • - D2D2C (disk-to-disk. • - Data archiving is the process of moving data that.
• - Data at rest is a term that is sometimes used to refe. • - A data breach is an incident in which sensitive, protec.
• - Data classification is the categorizati. • - A data center as a service (D. • - A data center. • - Data center bridging (DCB) describes.
• - Data center bridging (DCB. • - Data classification is the categorizati.
• - Data protection managemen. • - Data protecti. • - Data reduction is the process of minimizing the a.
• • - A storage replication service is a managed se. • - Database mirroring is the maintenance of. • - A data center as a service (DCaaS) provider will supply turnkey phy. • - Data center bridging (DCB) describes the four technology enhancements t. • - Desktop NAS (network-attached storage) is a device that. • - A DIMM (dual in-line memory module) is a double SIMM (single in-line.
• - A DIMM (dua. • - A disk image is a copy of the entire contents of a storag. • - Disk mirroring, also known as RAID 1, is the repl. • - Disk mirroring, also known as R. • - D2D2C (disk-to-disk-to-cloud) is an. • - D2D2C (disk-to-disk-to-cloud) is an. • - DNA storage is the process of encoding and decoding bin.
• - The Data Protection Act 1998 (DPA 1998) is an act of the Unit. • - Data protection management (DPM) is the administration of backup proces. • - DRBD (Distributed Replicated Block Device) is a Linux-based software. • • - A DIMM (dual in-line memo. • - A DIMM (dual in-line memo. • (Direct Internet Message Encapsulation) - a specification that defines a format for attaching files to Simple Object Access Protocol (SOAP) messages between application programs over the Internet. DIME is similar to but somewhat simpler than the Internet's MIME protocol.
• (DOM) - a programming interface from the W3C that lets a programmer create and modify HTML pages and XML documents as full-fledged program objects. • (Directory Services Markup Language) - an XML application that enables different computer network directory formats to be expressed in a common format and shared by different directory systems. • (Domino Extensible Language) - a specific version of Extensible Markup Language (XML) for Lotus Domino data. • - Novell's directory interchange software that uses XML to keep different directories synchronized. Spreadsheet Inventor Dan Bricklin on a Life in Computing Posted by If you use spreadsheets — and today the number of users that do so must be in the hundreds of millions — then every time you open a new workbook, edit a cell or calculate a formula, you can thank Dan Bricklin’s legacy.
Bricklin, an MIT graduate and Harvard MBA, developed with Bob Frankston back in 1979. The program not only gave rise to many of the elements of modern spreadsheet programs, selling over a million copies along the way, but, after its 1981 port, also helped the IBM Personal Computer become one of the most important new products of the 20 thcentury. Recently I spoke to Bricklin by phone about VisiCalc, its legacy, the rise of the PC generation and what’s happened since. First, I asked him to sketch a picture of financial management as it was when he wrote the code for what would become VisiCalc. “For hundreds of years, financial stuff was done on pen and paper and frequently on columns and rows with labels around them. [In the 1970s] we’d be doing it on paper or typing up things. That’s how you kept your books.
When they talked about book-keeping, it was exactly that: there were pages in books. Our first name for VisiCalc was Calcu-ledger because that helped explain what we were doing: providing calculations for general ledger.” Although the spreadsheet made his name, Bricklin had been largely concentrating on another software category that was to change the way the world worked.
“My background was in word processing but, back then, computerised printing of letters was mostly used in things like fundraising where you’d print one letter hundreds of times. The idea of using that equipment for a plain old letter by a typist they were just too expensive. The idea of a screen-based word processor was a new thing when I was working in the Seventies at Digital Equipment Corporation (DEC) but I had been exposed to systems like [drawing program] which were interactive programs that had started to become popular in the Sixties and Seventies in research institutions.
Computers were becoming important in newspapers so a reporter could type something in and see what it would look like but [for the majority of people] the idea of using a computer to do these things was new.” When Bricklin prototyped VisiCalc, he showed it to his Harvard professor who told him that his competition was calculating on the back of an envelope; if VisiCalc wasn’t faster, people would never use it. That notion helped make Bricklin a pioneer in another way: delivering a user experience (even before the term had been coined) that was intuitive so a new computer user would understand the new electronic tools. So, VisiCalc looked like a ledger book.
Similarly, in word processing, manual tools like scissors and glue became ‘cut’ and ‘paste’ features. Add in extra automation capabilities such as having words automatically wrap around lines of text and you had something that was revolutionary, in the days before even Wang and WordStar automated office tasks. But at the time, computers were rare, pricey and lacking a standard. “A person being able to buy a computer in a Radio Shack store was a new thing in the Seventies.
The only connection most people had to a computer was using automated teller machines. Timesharing with a terminal where you all shared this remote computer was being developed in the Sixties and started to become popular in the Seventies. People were starting to do financial forecasting but that would cost thousands of dollars a month, plus you’d need terminals. For sizeable companies doing MRP [manufacturing resource planning] that was reasonable, but it would cost $5,000 to $10,000 each for a word processing system of letter quality.” That pioneer environment explains why Bricklin had no great expectations for commercial success with VisiCalc but he was driven by an idea. “I came from the word processing world and in this What-You-See-Is-What-You-Get world I’d seen a mouse and was familiar with interactive systems. I think it’d seen an [early Xerox computer], played [a game for the DEC PDP-1], seen Sketchpad, knew APL and Basic.
The idea of having what we did with words and numbers on paper but with computation seemed pretty obvious; if there was a ‘eureka’ moment, that was it. “But I was in word processing and did word processing take off like crazy? Was it on every desk? Today, people hardly know how to write [in longhand] but in those days the idea that computers would be cheap enough. We knew what should be but we also knew from hindsight that acceptance was very slow.
I had seen the mouse in the 1970s, it was invented before that and didn’t come into acceptance until the 80s. So although we had something we saw was wonderful, we had no expectations.” With the benefit of hindsight though, grass shoots and signs were discernible.
“There were people making money out of software. [Mainframe database maker] Cullinane was the first pre-packaged software company to go public so we knew it was possible. But on the PC there were no [commercial] models. Almost nobody knew who Bill Gates was and he was maybe making a few million dollars a year.” Also, the economics of the day were very different as an Apple II “fully loaded” with daisywheel printer and screen cost about $5,000, the equivalent of about $18,000 today. This was also a time of scepticism about personal computing with the leading IT suppliers considering it a fad for hobbyists rather than a big opportunity to sell to business users. This attitude was underlined when Bricklin says he considered putting VisiCalc on DEC’s PDP-11 microcomputer before deciding on the Apple II. “I was thinking about it but the sales person wasn’t very aggressive.
It was classical. [DEC CEO] Ken Olsen saw PCs as wheelbarrows when he was selling pickup trucks.” That sort of attitude was unlikely to change Bricklin’s desire to set up his own company with Frankston rather than market his idea to the computing giants of the time. “I wanted to start a business and be an entrepreneur,” he recalls. “I had taken a few classes at Harvard; there weren’t many in those days but I took those that were on offer.” Although VisiCalc is sometimes presented as a smash hit that immediately launched the IBM PC, that notion is wrong on three points. VisiCalc was released on the Apple II in 1979, there were other ports before it was made available on the IBM PC, and the initial reaction from the wider world was lukewarm. “When it first came out, almost nobody but a few people in the computer press wrote about it. There was a humorous article about the National Computer Conference [scene of the VisiCalc launch] in the New York Times where the VisiCalc name was considered funny and the author was making fun of all the computer terms.
It then appeared in an announcement about my wedding in the Fall and my father-in-law was able to put some wording in about me being the creator of VisiCalc “We had ‘serious volume’ of 1,000 units per month for the first year. That’s nothing, that’s how many copies of a program are downloaded onto iPads every day, or every minute.” But by comparison to other business software for the personal computer, VisiCalc was a success and the most clued-in sales people at resellers used it to show what personal computers could do. “They knew that by demonstrating VisiCalc they could sell a PC it was a killer app. People at HP got it too.
One of my classmates at business school worked there and was making a small desktop computer that ran Basic and his boss put VisiCalc on that. Tandy started advertising about VisiCalc and sales started doing a lot better. By the time the IBM PC came out it was understood that it was a good thing and people in the business press started to say ‘can it run VisiCalc?’” If the laurels are to Bricklin and Frankston for creating the modern spreadsheet from the confluence of the rise in microcomputers, business interest and new software development languages, it was another program and company that cashed in on the full flowering of those trends. “When Lotus 1-2-3 came out [in 1983], the moon and stars were aligned for [Lotus founder and Bricklin’s friend] Mitch Kapor [to be successful] just as they had been for me to create VisiCalc,” says Bricklin, who adds that he knew the better program when he saw it. Turn another corner and things could have been different though. Microsoft’s dominance of PC software could have been even greater had it been smarter with its Multiplan product, Bricklin believes. Had Bricklin been more aggressive and the laws of the day been different, he could have pursued Lotus through the courts for the many features that arguably were derived from VisiCalc.
“The law in the US was that you couldn’t patent software and the chances were one in ten you could try to sneak it through and call it a system,” he recalls. In truth, Bricklin would make an unlikely litigant and says he never considered such a path. He is proud, rather, that his legacy still looms large, even if he didn’t make the millions that others did. The tech investor Ben Rosen called VisiCalc “the software tail that wags (and sells) the personal computer dog” and there’s no doubt that it played a big part in what happened later to our digitising universe. While some pioneers skulk and criticise others that followed them and were successful, Bricklin appears to have no trace of bitterness. He remains a staunch fan of Microsoft and Excel, a product that remains a cash machine and still bears the stamp of VisiCalc, 35 years on.
“Doing VisiCalc, I had to come up with the essence of what you need in 32K of RAM and our notion of what was important was correct, it turned out,” he says. But the power and richness of Excel are remarkable, he says, rejecting the notion that the Redmond company is guilty of creating bloatware. “Microsoft came from engineers building things: programmers, programmers, programmers — and the hearts and minds of programmers mattered a lot to them. People want to customise things, make it right for what their problem is. It’s the difference between being a carpenter and being an architect — one size does not fit all. “Microsoft built systems that could be customised, so users could replace that part themselves and it listened to a lot of people and provided what they wanted, all the bells and whistles. People say you end up with bloatware and only 10% of the features get used by any user but that 10% is different for a lot of users.
Apple went for smaller number of people and that’s OK because there’s Microsoft for the rest. [Microsoft] had business practices that people didn’t like but is that different than other companies in other industries? Not necessarily.
“As a child of the Sixties I think of Bob Dylan: ‘the loser now will be later to win’. It goes in cycles. The founder of Intel [Andrew Grove] said it: Only the Paranoid Survive and you only have so much time [at the top].” If Bricklin was before his time with VisiCalc, he was also early onto new trends in user input, creating pen-operated applications at Slate Corporation in the early 1990s and in 2009, a app for the “magical” iPad he so admires.
“I decided I wanted to get into that [iOS] world because there were times when I wanted to get something down and if I write 5 and it’s a bit off, that’s OK. But if I did that on a keyboard and it’s a 6, that’s no good for a telephone number. I got to learn what’s it’s like, that world of app stores and so on, and I did all the support so I got to see what people needed.” That took him to the latest stage of his journey, as CTO for a company specialising in using HTML5 to make software multiplatform. “I saw businesses were going to replace clipboards with tablets and that’s why I decided to join.
I couldn’t do everything on my own because there’s so much at the back end you need to do but I wanted to innovate at the front end. Being able to customise is something that’s exciting to watch but it takes time. You’d think that in companies with billions of dollars, why would people be carrying around procedure manuals instead of on a digital reader? [Automating cross-platform capabilities] is extremely important in business.
You’d think that most companies would have started taking great advantage of custom mobile opportunities internally, but most haven’t gotten there yet.” Bricklin remains awestruck by changes he has seen in a lifetime of computing that has made him a sort of smarter or for the binary age — a person who was around at some of the biggest the zeitgeist moments in computing history. “When I was working in word processing in my early twenties, I was doing programming for a person who worked for and the year I was born as it turned out, Forrester showed the computer on TV and that was the first time the general public got to see a computer in action, in this video from 1951 [YouTube clip.
Bricklin’s boss stayed up for days making sure it was ready for demo and you can see him there in the background [starting at 4.01]. Those were computers that were the size of big rooms and I was working with him on something you could fit in a desk. And now it’s in the pocket and on a watch soon. This is a progression I’ve seen my whole life and it’s a joy each time.” Bricklin seems content to be recognised as a founding father of the segment, rather than a Rockerfeller.
“If you look at the old basketball players, they didn’t make as much either,” he says, philosophically. “But we wanted to bring computing to more people and we did that.” Bricklin delights in the fact that science fiction has become reality and that naysayers have been disproved. It gives him pleasure to think that that those who mocked the personal computer as a place to store recipes now Google their ingredients to automatically generate recipes. “In they’re using a tablet that looks just like an iPad and it’s this magical device. The crystal ball of fiction is now real. In The Wizard of Oz they had this remote thing; the witch could see things at a distance, control things at distance. This is something you can now buy in a store: a drone-controlling iPad.
You can communicate with other people in real time and you can control it with a wave of your hands.” He ponders the rise of the PC and the changes it wrought as people were freed to create, compose, calculate and pay. “God!” he exclaims, stretching the syllable in wonder, his voice rising to a crescendo. “It was so exciting to see the thing you believe in succeed and to be accepted. My daughter as a youngster once said, ‘Daddy, did they teach you spreadsheets at school?’ and then, after a few seconds corrected herself.
‘Wait a minute’ That’s really cool to see people use things that we thought should be used. To be vindicated, that was pretty cool. Sony Ericsson Hcb 100 Manual. ” is Editorial Director at IDG Connect Link. Words to go: Data center design standards bodies by Need a handy reference sheet of the various data center standards organizations?
Keep this list by your desk as a reference. Several organizations produce data center design standards, best practices and guidelines. This glossary lets you keep track of which body produces which standards, and what each acronym means.
Print or bookmark this page for a quick reference of the organizations and associated websites and standards that data center designers and operators need to know. •: The American Society of Heating, Refrigerating and Air-Conditioning Engineers produces data center standards and recommendations for heating, ventilation and air conditioning installations. The technical committee develops standards for data centers' design, operations, maintenance and energy efficiency. Data center designers should consult all technical documents from ASHRAE TC 9.9: Mission Critical Facilities, Technology Spaces and Electronic Equipment. • BISCI: The Building Industry Consulting Service International Inc. Is a global association that covers cabling design and installation. ANSI/BICSI 002-2014, Data Center Design and Implementation Best Practices, covers electrical, mechanical and telecommunications structure in a data center, with comprehensive considerations from fire protection to..
•: The BRE Environmental Assessment Method (BREEAM) is an environmental standard for buildings in the U.K. And nearby countries, covering design, construction and operation.
The code is part of that takes into account economic and social factors as well as environmental. It is managed by BRE Global, a building science center focused on research and certification. •: The Green Grid Association is well-known for its metric, defined as power usage effectiveness or efficiency.
PUE measures how well data centers use power by a ratio of total building power divided by power used by the IT equipment alone. The closer to 1 this ratio comes, the more efficiently a data center is consuming power. Green Grid also publishes metrics for water () and carbon () usage effectiveness based on the same concept.
• IDCA: The International Data Center Authority is primarily known as a training institute, but also publishes a holistic data center design and operations ranking system: the Infinity Paradigm. Rankings cover seven layers of data centers, from location and facility through data infrastructure and applications. •: The Institute of Electrical and Electronics Engineers provides more than 1,300 standards and projects for various technological fields. Data center designers and operators rely on the network cabling standard IEEE 802.3ba, as well as IEEE 802 standards, for local area networks such as IEEE 802.11 wireless LAN specifications. •: The International Organization for Standardization is an overarching international conglomeration of standards bodies. Releases a wide spectrum of data center standards, several of which apply to facilities. ISO 9001 measures companies' capabilities.
ISO 27001 certifies an operation's security best practices, regarding physical and data security as well as business protection and continuity efforts. Other ISO standards that data center designers may require include environmental practices, such as ISO 14001 and ISO 50001. •: The Leadership in Energy and Environmental Design is an international certification for environmentally conscious buildings and operations managed by the U.S. Green Building Council.
Five rating systems -- building design, operations, neighborhood development and other areas -- award a LEED level -- certified, silver, gold or platinum -- based on amassed credits. The organization provides a data-center-specific, as the LEED standard includes adaptations for the unique requirements of data centers. • NFPA: The National Fire Protection Association publishes codes and standards to minimize and avoid damage from hazards, such as fire. No matter how virtualized or cloudified your IT infrastructure, fire regulations still govern your workloads. NFPA 75 and 76 standards dictate with obstructions like curtains or walls.
NFPA 70 requires an for the data center to protect emergency respondents. • NIST: The National Institute of Standards and Technology oversees measurements in the U.S. NIST's mission includes research on nanotechnology for electronics, building integrity and diverse other industries.
For data centers, NIST offers recommendations on authorization and access. Refer to special publications 800-53, Recommended Security Controls for Federal Information Systems, and SP 800-63, Electronic Authentication Guideline. •: The Open Compute Project is known for its server and network design ideas. But OCP, started by Internet giant Facebook to promote open source in hardware, also branches into data center design.
OCP's Open Rack and optical interconnect projects call for 21 inch rack slots and intra-rack photonic connections. OCP's data center design optimizes thermal efficiency with 277 Volts AC power and tailored electrical and mechanical components.
• OIX: The Open IX Association focuses on Internet peering and interconnect performance from data centers and network operators, along with the content creators, distribution networks and consumers. It publishes technical requirements for that support them. The requirements cover designed resiliency and safety of the data center, as well as connectivity and congestion management.
• Telcordia: Telcordia is part of Ericsson, a communications technology company. The Telcordia GR-3160 Generic Requirements for Telecommunications Data Center Equipment and Spaces particularly relates to telecommunications carriers, but the best practices for network reliability and organizational simplicity can benefit any data center that delivers applications to end users or host applications for third-party operators. Deals with environmental protection and testing for hazards, ranging from earthquakes to lightning surges. • TIA: The Telecommunications Industry Association produces communications standards that target reliability and interoperability. The group's primary data center standard,, covers network architecture and access security, facility design and location, backups and redundancy, power management and more. TIA certifies data centers to ranking levels on TIA-942, based on redundancy in the cabling system. •: The Uptime Institute certifies data center designs, builds and operations on a basis of reliable and redundant operating capability to.
Data center designers can certify plans; constructed facilities earn tier certification after an audit; operating facilities can prove fault tolerance and sustainable practices. Existing facilities, which cannot be designed to meet tier level certifications, can still obtain the from Uptime.
Hola Nemesis, yo descargo videos de youtube usando FireFox, con el complemento “Download helper” mas “converter helper”, este ultimo convierte los videos a varios formatos ya que se descargan en formato Flv. En el menu de Firefox das click en “Herramientas/complementos/obtener complementos: en la caja de busqueda escribes Download Helper y ahi te aparecera un resultado de la busqueda en el cual debes dar click en instalar. Tambien te aparecera un descargador especial para youtube, pero no lo he usuado. Bueno, ahi tienes unas opciones para descargar desde youtube. Respecto a que hacer con la portatil se debe abrir uno de ls compartimientos inferiores alli encontraran la tarjeta inalambrica con dos conectores mini(no recuerdo), a estos se cnecta un pigtail con conector N al final y listo se conecta a la antena q deseemos utilizar, existen varios tutoriales para hacer antenas direccionales (pringles, latas, quad), omnidireccionales (pvc). Si desean utilizar un softaware para ver q caracteristicas radio electricas tendran sus antenas pueden usar el antenna magus, desafortunadamente es de pago:(, pero si alguien tiene una medicina para eso q la comparta.
Hay software como 4nec que tambien es util.